In this article, we explore general recommendations and best practices for safeguarding a comprehensive IT architecture. The following use cases are highlighted for protection and optimization:
- Websites / web applications (standard HTTP requests)
- API endpoints (HTTP requests with
content-typeJSON) - SSL VPN endpoints (TCP and UDP segments)
- Data Center with a CIDR notation /24 (IP Prefix)
Cloudflare can be instrumental in enhancing security and streamlining operational complexity by consolidating multiple tools into a unified, integrated platform. Real-world case studies illustrating organizations benefiting from this approach include Carrefour (the eighth-largest retailer globally by revenue) and Chrono24 (one of the world’s largest online marketplaces for luxury watches).
Other interesting case studies are: Eurovision, Discord, Republic of Estonia Information Security Authority, DHL Parcel, C&A, and 9GAG among others.
OSI Layers#
Here is a visual representation of mapping Open Systems Interconnection model (OSI model) Layers to Cloudflare solutions:
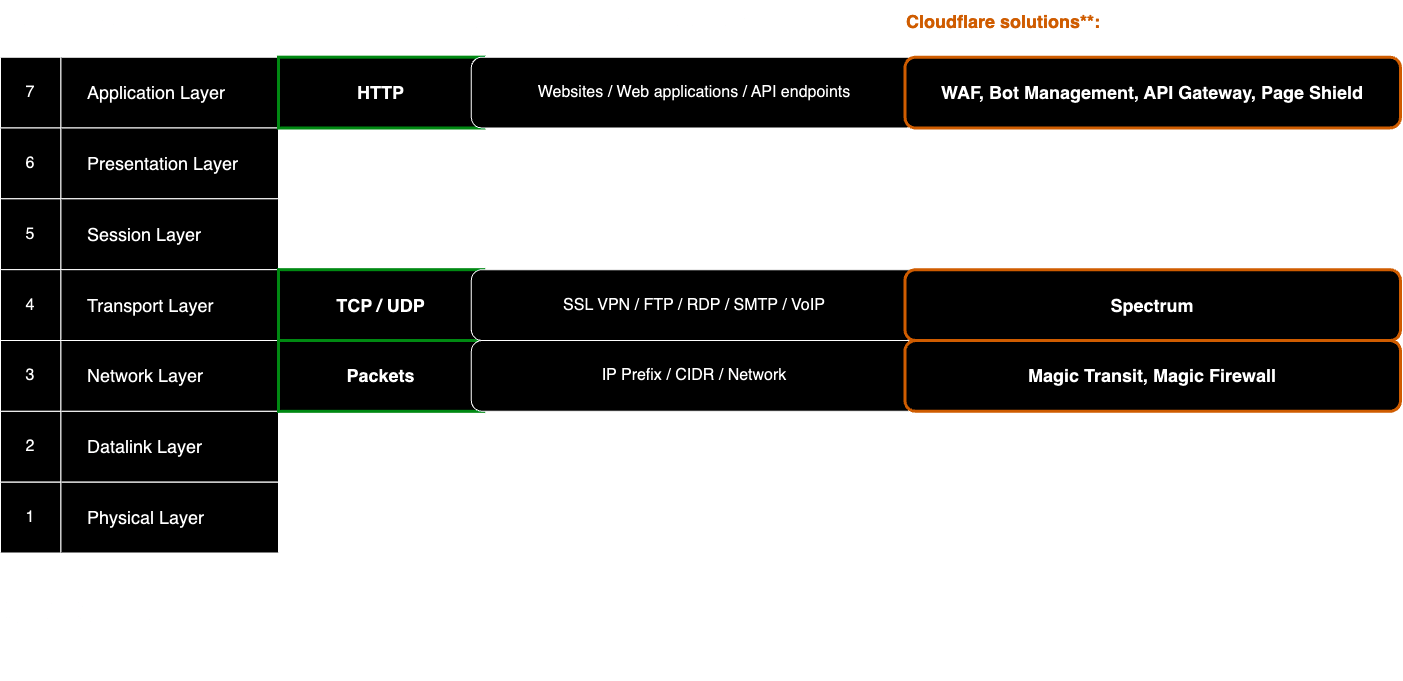
This diagram provides an overview of how Cloudflare solutions effectively correspond to different OSI layers. High-level examples and use cases on these OSI layers are elaborated in this article, offering a general understanding of the practical applications of Cloudflare across the networking stack.
Getting Started#
Authoritative DNS#
Let’s begin by designating Cloudflare as your Authoritative DNS provider using the Full Setup, granting you comprehensive control over all DNS-related aspects. Alternatively, opt for a CNAME Setup or Partial Setup.
Note: The hosting provider (origin server) and its location are usually inconsequential as long as it is accessible over the Internet.
Once your Zone is added, proceed to proxy (orange-cloud) your DNS records. Note that the /cdn-cgi/ endpoint is then added to your domain.
Note: Safeguard your origin IP address by adhering to Cloudflare’s recommendations, including the rotation of IP addresses and concealing unproxied DNS records through the use of non-standard names for these records. Learn more about this in the Protect origin IP address guide.
This initial setup seamlessly incorporates essential security features, providing:
Built-in DNSSEC, Automatic HTTPS Rewrites, and HTTP Strict Transport Security (HSTS) with one-click.
Common adjustments to HTTP request and response headers (i.e. security headers) via Managed Transforms with one-click.
Email Security DNS Wizard with DMARC Management to easily and quickly configure Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication Reporting and Conformance (DMARC).
Free, privacy-first Cloudflare Web Analytics to monitor timing metrics and Core Web Vitals.
Free Universal SSL Certificate automatically deployed, managed and renewed by Cloudflare.
Pre-configured WAF Managed Rules immediately deployable with one-click.
Unmetered and unlimited DDoS protection at layers 3, 4, and 7 of the OSI model for proxied hostnames. Review the DDoS attack coverage.
Note: Follow Cloudflare’s recommendations on third-party services and Cloudflare DDoS protection.
Origin Server Security#
Cloudflare serves as a robust reverse proxy, managing the connection between clients/end-users and the origin server.
When a client makes a standard request to the origin server, Cloudflare sits in-between, ensuring a layer of security and configuration checks.
Note: It is crucial to channel all traffic through Cloudflare before reaching the origin to optimize security measures, masking the origin IP address, conserve origin bandwidth, and efficiently utilize origin resources. Cloudflare essentially becomes the gatekeeper (proxy).
My personal favorite approach involves deploying the Cloudflare Tunnel by installing the cloudflared daemon on the origin server. This setup establishes outbound-only connections to Cloudflare’s global network, eliminating the need for the origin server’s IP address, firewall configuration or any port forwarding. Instead, the Cloudflare Tunnel hostname becomes the designated origin.
Bear in mind that it is possible to configure Static IPs or Bringing Your Own IPs (BYOIP) as Ingress IPs for the client, enabling the allowlisting of these IPs for access. Moreover, by leveraging Aegis, you can establish dedicated Egress IPs connecting from Cloudflare to the Origin Server. This enables the allowlisting of these specific IPs on the Origin Server, allowing for the imposition of network Access Control Lists (ACLs) to exclusively permit traffic originating from these IPs into the network.
For comprehensive details, review the protect your origin server developer documentation, including which network ports are proxied by default.
Flow of HTTP Requests#
Cloudflare runs one of the largest global anycast networks in the world. Traffic within the Cloudflare Point of Presence (PoP), between data centers, and between the Cloudflare network and a customer’s origin is encrypted when in transit. The customer has the option and flexibility to select which encryption mode and which cipher suites to use. In addition, all request and response processing within a Cloudflare PoP takes place in memory – through machine inspection: use of headless servers and technical measures to prevent any human access. Nothing is written to disk except for eligible content for caching or Cache Rules configured by the customer, and all cache disks are encrypted at rest.
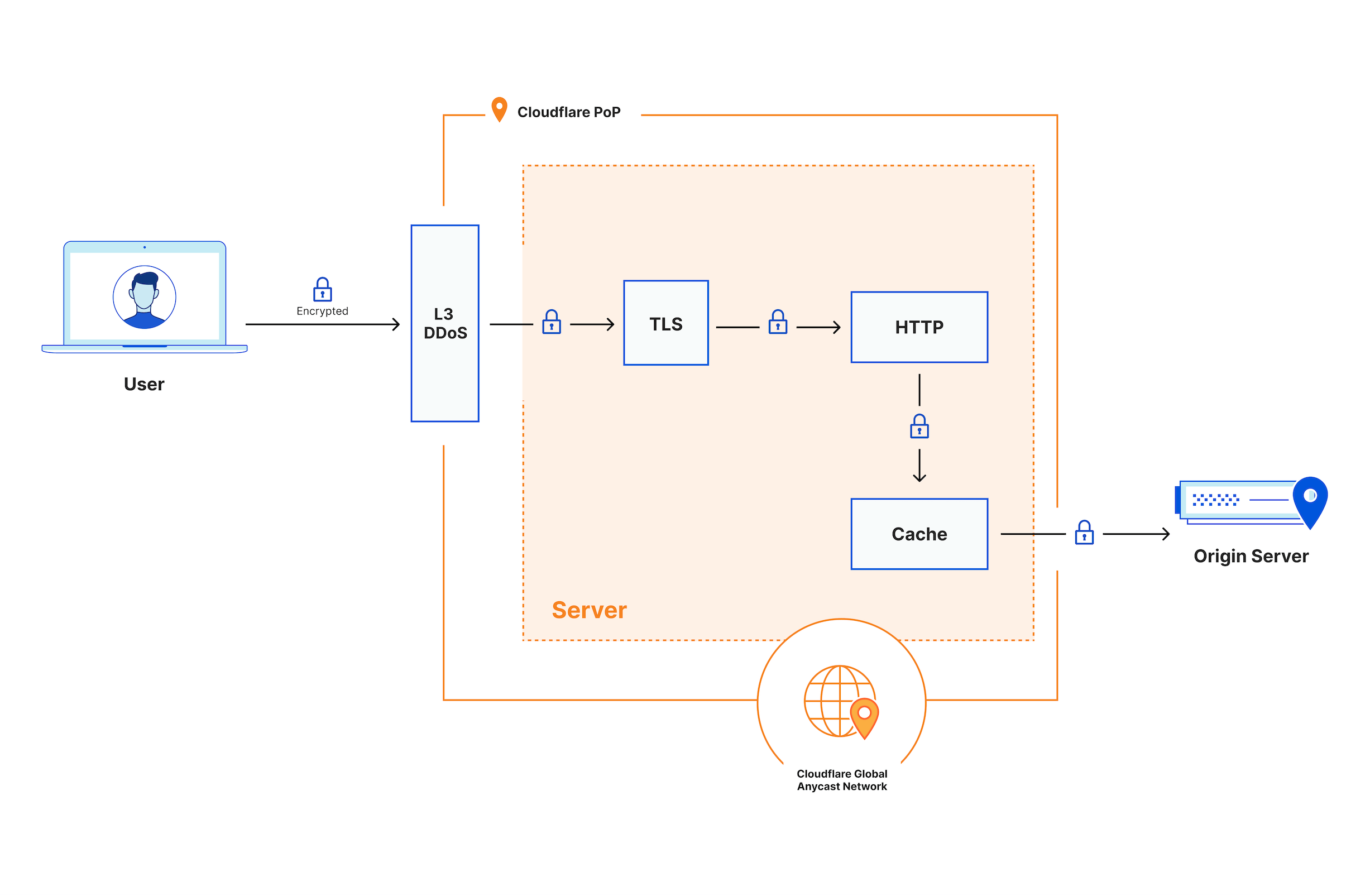
On a high-level, once the device of an end user connects with a Cloudflare PoP – no matter which one –, the request is processed in the following way:
- Certain types of requests that can be used for cyber attacks are immediately dropped based on the addressing information (Layer 3 / Network Layer).
- Next, the encrypted request is decrypted and inspected using the business logic requested and enabled by the customer, such as i.e. the products Configuration Rules, Web Application Firewall (WAF) Custom Rules, Rate Limiting Rules, and so on – following the traffic sequence and phases. This enables the detection and prevention of a variety of different types of cyber attacks and malicious traffic, including Layer 7 / Application Layer DDoS attacks, automated bot traffic, credential stuffing, and SQL injection among others.
- The inspected request is then passed to the cache module. If the cache can fulfill the request with a cached copy of the content, it does so; if not, it forwards the request to the customer’s origin server. Traffic between the Cloudflare PoP and the origin server is encrypted, unless the customer decides to use a different encryption mode.
- When the response comes from the customer’s origin server, any static and eligible content is cached onto encrypted disks. The response then goes back through the business logic to the user across the Internet. By default, Cloudflare performs TLS termination globally in every PoP, where the Internet end user connects to a website or application behind Cloudflare. However, customers can configure Regional Services – a Data Localization Suite (DLS) feature – to control in which regions the processing and TLS termination occurs.
Use Cases#
L7 HTTP: Web Applications#
Users engage with websites and web applications through HTTP requests at the Application Layer (Layer 7).
By routing HTTP traffic through Cloudflare, you can leverage a variety of solutions to enhance security, performance, and overall web application functionality.
Use Case: Security#
SSL/TLS – Edge Certificates
By choosing Cloudflare as your Authoritative DNS provider, your Zone/Domain automatically receives an Universal SSL Certificate. For enhanced customization and coverage of multiple levels of subdomains, it is advisable to consider Advanced Certificates. Cloudflare seamlessly manages and renews these certificates automatically.
It is generally recommended to utilize the Full (strict) encryption mode in conjunction with Authenticated Origin Pulls (mTLS) using your own Custom Certificate.
Note: For any compliance-related requirements, review the custom cipher suites. Additionally, review the Developer Documentation on protect your origin server.
Web Application Firewall (WAF) – automatic protection and flexibility
Effortlessly enhance your security posture with one-click deployment of pre-configured WAF Managed Rules across your entire domain or a specific scope of incoming requests. This provides peace of mind against various types of attacks. Nevertheless, it is advisable to review the individual rules in Cloudflare Managed Ruleset and customize pre-defined rules to suit your specific needs, as well as optimizing the paranoia level of the OWASP Core Ruleset to prevent potential false positives.
Generally recommended Managed Rules that should be manually enabled are:
- XSS, HTML Injection with Rule ID
882b37d6bd5f4bf2a3cdb374d503ded0. - Anomaly:URL:Path - Multiple Slashes, Relative Paths, CR, LF or NULL with Rule ID
6e759e70dc814d90a003f10424644cfb. - Anomaly:Body - Large with Rule ID
ee922cf00077462d9f2f7330b114b839. - Anomaly:Port - Non Standard Port (not 80 or 443) with Rule ID
8e361ee4328f4a3caf6caf3e664ed6fe.
Note: Every application is uniquely constructed, and therefore, the enabled individual Managed Rules should undergo prior review to ensure that essential functionalities are not disrupted.
Start by gaining comprehensive visibility into all activities on your domain through an analysis of Security Analytics. Subsequently, craft highly specific WAF Custom Rules employing the SKIP action. This step is crucial for allowing internal, trusted and familiar traffic, particularly for internal API endpoints and Verified Bots, thereby minimizing the risk of false positives in other Custom Rules. You can create lists to simplify the setup.
Once this foundation is established, proceed to create more generalized Custom Rules to proactively mitigate potential attacks or implement measures to block or challenge specific types of traffic. This tiered approach ensures a nuanced and effective strategy for optimizing security while minimizing disruptions to legitimate operations.
Note: we normally do not want to block the
/cdn-cgi/endpoint or Cloudflare crawlers; or internally trusted traffic.
Exercise precise control over which requests are blocked, challenged, skipped, or logged by leveraging the flexibility of WAF Custom Rules. Explore common use cases for custom rules for practical examples, and be mindful of the phases and the order of rule evaluation, considering the associated actions.
Another peace of mind configuration is to simply block Managed Lists with WAF Custom Rules.
Note: Consider configuring Custom Error Responses for your WAF Custom Rules, or Configuring Custom Pages (Error and Challenge), in order to establish a coherent branding across all custom pages and responses.
There’s also the option to inspect HTTP request body fields (payloads) / Payload Inspection. The encrypted payloads can be found in the Metadata field in Firewall events logs.
For advanced threat mitigation, including potential zero-day attacks – like from SQL injection (SQLi), Cross-site scripting (XSS), and Remote Code Execution (RCE) attacks –, take advantage of the WAF Attack Score. For instance, create a WAF Custom Rule to block requests with a WAF Attack Score below 50 (cf.waf.score lt 50), indicating a likely attack (likely_attack). This additional layer of defense fortifies your security measures against evolving and sophisticated threats.
Rate Limiting – restricting the number of requests
Enhance security further by integrating the deployment of WAF Managed Rules and WAF Custom Rules with Rate Limiting Rules. Rate Limiting empowers you to set specific limits for requests that meet defined criteria and determine the action to take when those limits are exceeded. Explore common best practices and rule examples to fortify your defenses, whether you’re safeguarding REST or GraphQL APIs or controlling the frequency of operations, among other scenarios. In order to find an appropriate rate limit, review the Security Analytics.
Bot Management – mitigate automated traffic
To attain in-depth visibility into automated traffic, particularly content scrapers, credential stuffing, inventory hoarding, and other bots, it is recommended to acquire a Bot Management subscription. This subscription unlocks the utilization of fields such as BotScore and JA3 Fingerprint in WAF Custom Rules and Rate Limiting Rules, providing added flexibility for crafting specific rules.
Note: In certain scenarios, certain requests are exempt from scoring. The
__cf_bmBot Management Cookie serves as a functional cookie that enhances scoring but can be disabled upon request. Moreover, API requests are considered automated traffic.
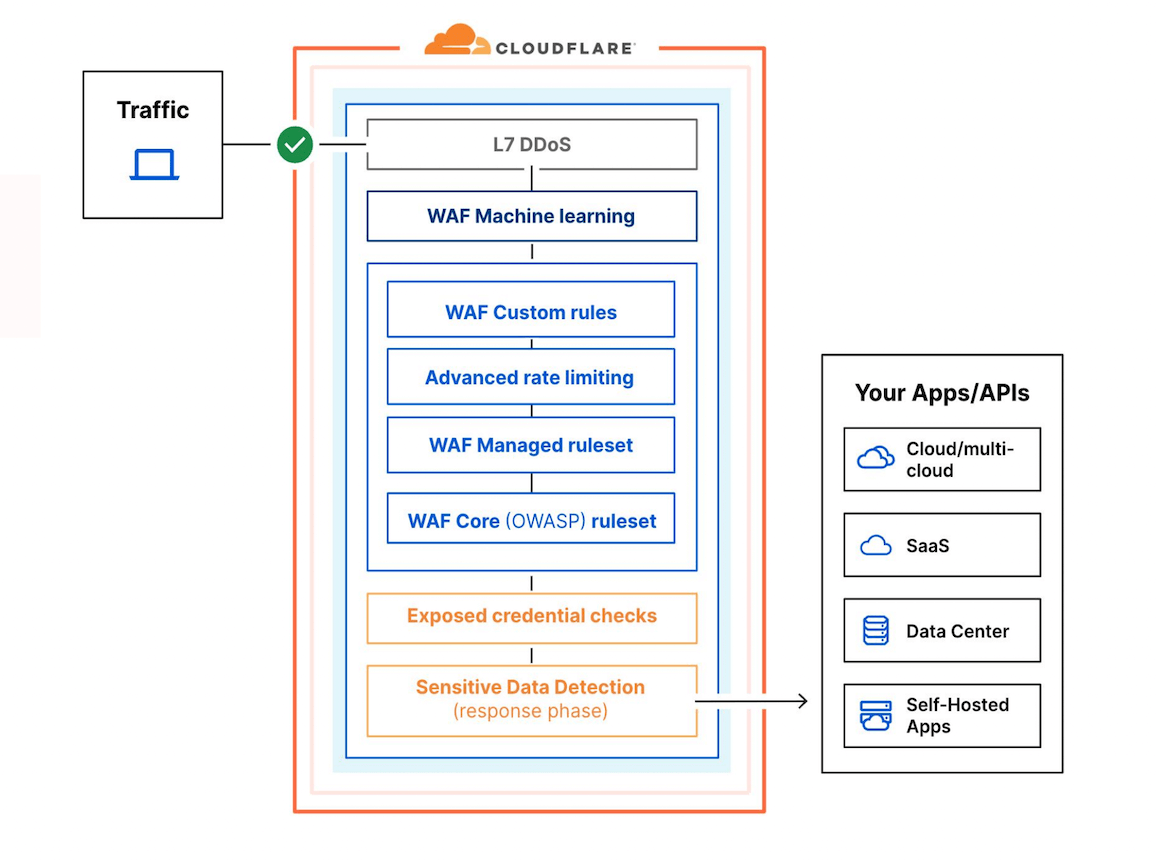
Image source: Cloudflare WAF Product Brief
Turnstile – CAPTCHA alternative
If you’re seeking an alternative to CAPTCHA or unable to invest in the more comprehensive Bot Management solution, consider utilizing the privacy-preserving Turnstile as a safeguard against malicious bots. Learn more about it’s capabilities in the Cloudflare is free of CAPTCHAs; Turnstile is free for everyone blog post. Furthermore, you have the option to seamlessly integrate Turnstile into the WAF. This allows web administrators to incorporate the Turnstile code snippet into their websites and subsequently configure the Cloudflare WAF to handle these requests.
WAF Content Scanning – malware scanning
Moreover, for those seeking to scrutinize content uploaded to an application, WAF Content Scanning can prove beneficial. When activated, content scanning endeavors to identify content objects, including uploaded files, and scans them for malicious signatures such as malware. It is advisable to establish a detailed WAF Custom Rule, specifying the URI Path where the content is uploaded, to promptly block any detected malicious content objects.
Page Shield – third-party script management
Page Shield can display third-party scripts being loaded, when and where on your website, also allowing you to define policies to allow certain scripts to be loaded. In the near future, related potential CVEs will also be displayed.
Use Case: Performance#
Effortlessly enhance your website’s performance with a single click by implementing a range of speed optimizations. These include features such as Brotli compression, HTTP/3 (with QUIC), Auto Minify, and more.
Moreover, improve SEO by following Cloudflare’s recommendations.
Cloudflare Fonts – compliant and fast fonts
Cloudflare Fonts transforms your website’s HTML by eliminating Google Fonts links and substituting them with inline CSS. This strategic adjustment ensures that fonts are delivered from your domain through Cloudflare’s infrastructure, leading to optimized performance and improved user privacy.
Argo Smart Routing – efficient routing
Experience advanced Layer 7 efficiency with Argo Smart Routing, streamlining the routing of traffic along the most optimal network path from Cloudflare to the origin server — also achievable with just one-click.
Zaraz – third-party tool manager
Unlock precise control over cookie storage (consent management) and information sharing with third party scripts by leveraging the capabilities of Zaraz and it’s privacy settings. Here it’s important to point out the usage of Google Analytics with Cloudflare. Review my Cloudflare Zaraz article for some examples.
Cache Rules – caching customization
Configuring and adapting Cache Rules is key to taking advantage of the global Cloudflare Content Delivery Network (CDN) and improving delivery of eligible assets. The CF-Cache-Status response header value we are looking for is HIT. The CF-RAY response header shows from which Cloudflare PoP (IATA 3-letter airport code) the asset was delivered.
Generally, the following Cache Rules are commonly used:
- Low Edge Cache TTL: Ideal for rapidly changing content, revalidation and update of content.
- Cache by Status Code: Enables selective caching based on status code, such as caching only
200responses or customizing caching for errors. - Cache Reserve Eligibility: Useful for seldom-changing stale content like favicons or logos, requiring the implementation of Cache Reserve.
- Proxy Read Timeout: Designed for slow origins that perform extensive computations before responding.
- Bypass Cache: Appropriate for dynamic or user-specific content, such as data from API endpoints, ensuring it is not cached. Do not cache sensitive paths or Personal Identifiable Information (PII).
Keep in mind the order and priority when creating the Rules.
Note: Cloudflare’s global network and direct peering with multiple providers contributes to exceptional network performance.
Image Optimization – optimize and transform images on the fly
Furthermore, you can explore Image Optimization features such as Image Resizing and Polish. Polish, a convenient one-click enhancement, not only optimizes images but also converts the content-type of PNG and JPEG images to WebP for improved efficiency. On the other hand, Image Resizing provides enhanced flexibility and granularity in image transformations. You can implement Image Resizing using URL Format (either directly in the HTML code with srcset or through Transform Rules), or alternatively, through Workers.
Performance Measurement
Delve into detailed performance metrics by exploring various fields within the HTTP request dataset accessible through Logpush. Gain valuable insights into aspects such as:
- OriginResponseHeaderReceiveDurationMs
- OriginTCPHandshakeDurationMs
- OriginTLSHandshakeDurationMs
- ClientTCPRTTMs
For a comprehensive analysis, the GraphQL Analytics API provides access to the httpRequestsAdaptiveGroups dataset, showcasing additional performance-related metrics, including:
- Time to First Byte (TTFB) (edgeTimeToFirstByteMs)
- Origin DNS lookup time (edgeDnsResponseTimeMs)
- Origin Response Time (originResponseDurationMs)
Note: while the Time to First Byte (TTFB) metric holds significance for API endpoints, it’s important to note that when assessing websites or web applications, other more meaningful metrics, such as Core Web Vitals, should take precedence. Core Web Vitals offer a more comprehensive evaluation of the real user experience, as described in the Are you measuring what matters? A fresh look at Time To First Byte blog post. Therefore, for a holistic understanding of web performance and user satisfaction, it is advisable to prioritize metrics that align closely with the actual user experience. This is why Observatory can be a great start.
L7 HTTP: API endpoints#
In today’s digital landscape, a significant portion of Internet traffic is automated or API-driven, reflecting the increasing reliance on API-driven applications. According to Cloudflare, over half of dynamic traffic is API-related and continues to grow. Developers must effectively manage APIs to support diverse functionalities, necessitating continuous monitoring and authentication for each request.
Note: API traffic encompasses any HTTP/S request with a response
content-typeofapplication/jsonorapplication/*.
This is precisely where API Shield becomes invaluable. Serving as a central hub for securing, managing, and monitoring API traffic, API Shield offers the following key features:
- Discovery: identify and monitor the API endpoint landscape.
- Layer 7 Security: protect against abusive attacks, including application DDoS and brute-force attempts.
- Schema Validation (Positive API Security): automatically validate OpenAPI v3 schemas for enhanced API protection.
- Volumetric Abuse Detection: stop volumetric API abuse through advanced anomaly detection mechanisms and Rate Limiting.
- Mutual TLS (mTLS): deliver robust authentication for mobile and IoT APIs.
- Sensitive Data Detection: safeguard against data leaks by continuously scanning response payloads for sensitive information.
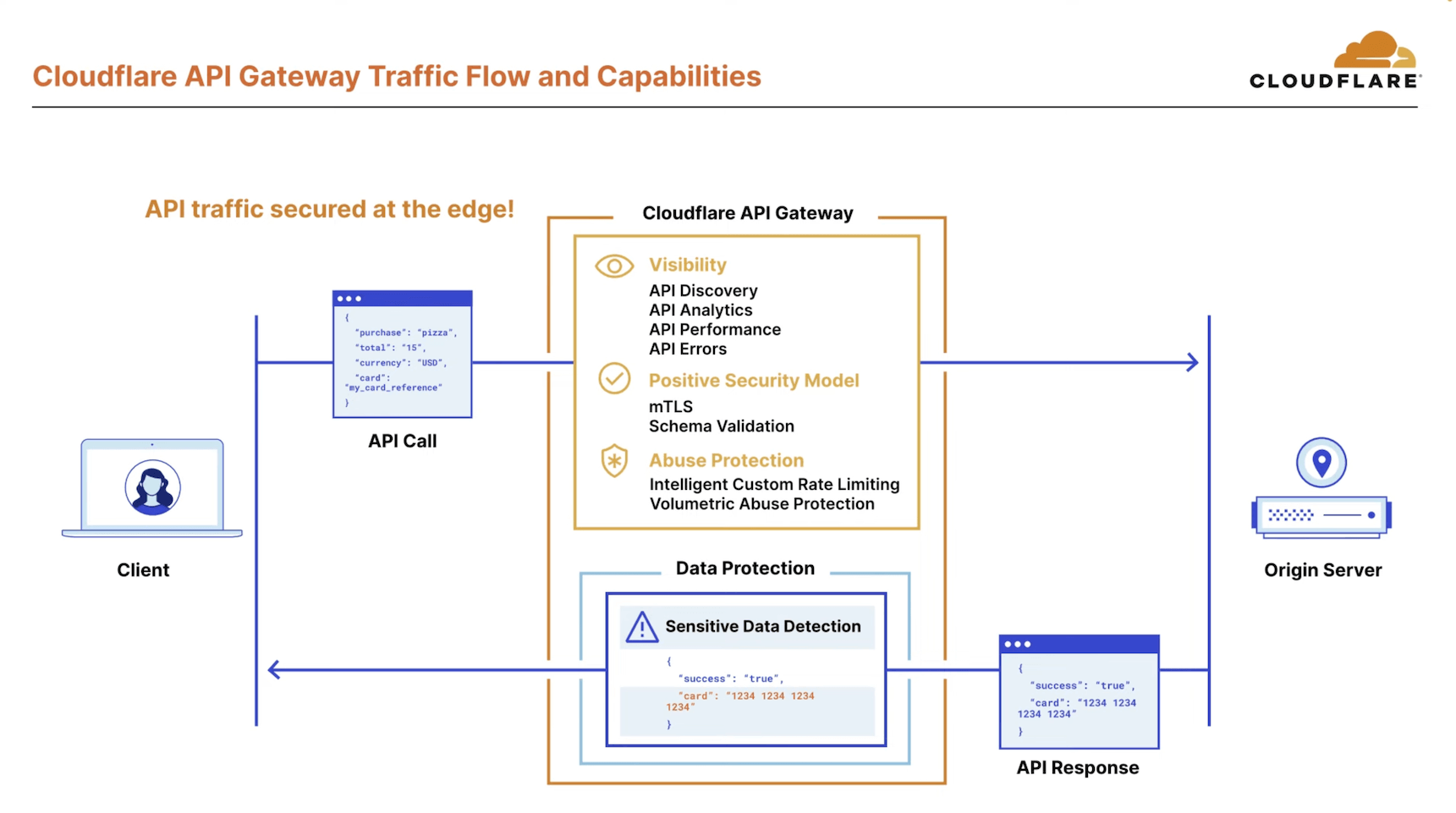
Image Source: Cloudflare YouTube video
Use Case: Observability#
Many development teams face challenges in effectively managing or cataloging their APIs. Cloudflare’s API Discovery comes to the rescue by aiding in mapping and comprehending your attack surface.
The API Dicovery feature meticulously catalogs all identified API endpoints. It utilizes user-specified Session Identifiers, such as headers or cookies, alongside Machine Learning-based Discovery. These insights can then be seamlessly integrated into Endpoint Management, facilitating in-depth analytics and comprehensive oversight.
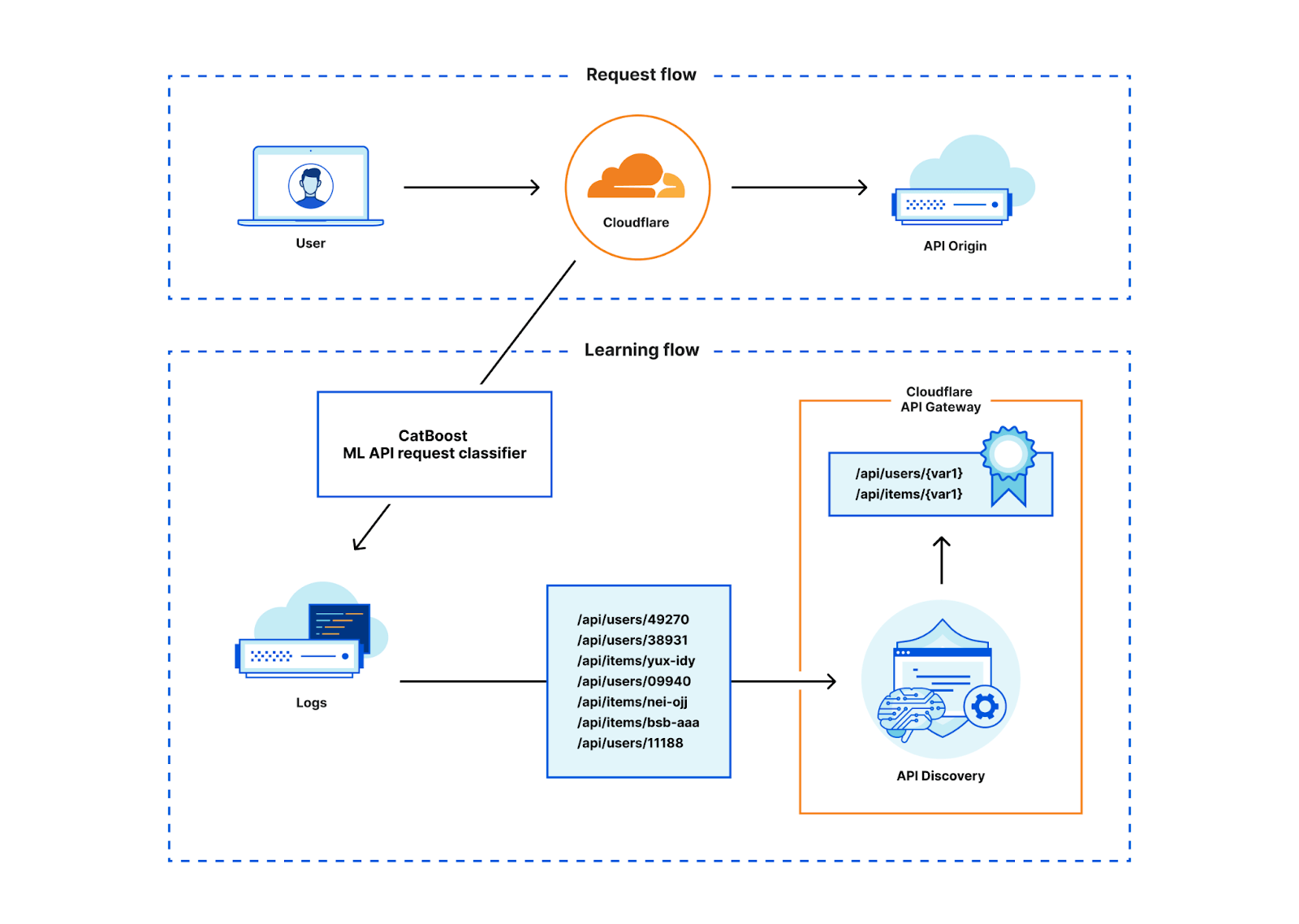
Image Source: Cloudflare blog post
Note: it takes approximately 24 hours and a minimum of several hundreds of API requests after adding an endpoint for Cloudflare to learn the API schema and patterns.
Use Case: Positive Security Model#
API Schema Validation – compliant incoming traffic
The compilation of all anticipated formats for every API endpoint within an API is termed an API schema. Utilizing API Schema Validation proves highly effective in safeguarding against bug exploitation, invalid API requests, and malicious payloads. This validation ensures that the body, path, and query string of a request contain the expected information for a given API endpoint in the anticipated format.
You have the flexibility to either manually upload API schemas or apply learned schemas after some time. Additionally, you can create an interactive documentation portal (API catalog) using the developer portals. This empowers your team with a comprehensive resource for understanding and interacting with the APIs, promoting better development practices and enhanced security measures.
mTLS – bidirectionally secure and trusted traffic
In standard HTTPS communication, the server provides the TLS certificate during the SSL handshake to secure the connection. However, in mutual TLS (mTLS), clients are required to provide a certificate to the server, establishing a logical checkpoint that needs to be configured with the server. When utilizing Cloudflare to proxy traffic, Cloudflare assumes the role of the server in communication with clients. Consequently, you can enable the mTLS feature with Cloudflare without the necessity to configure it with your servers. As long as the client presents the correct certificate without triggering additional security checkpoints, Cloudflare will grant access to the server.
Note: in this section, we are referring to the connection established by the end user to Cloudflare. If you are interested in implementing mTLS not only from the end user to Cloudflare but also from Cloudflare to the origin server, where the origin server verifies the client certificate provided by Cloudflare, review Authenticated Origin Pulls (mTLS).
L4 TCP/UDP#
Spectrum – global TCP and UDP proxy
Cloudflare is typically used as an anycast reverse proxy for HTTP/S traffic. To extend its capabilities to proxy TCP/UDP services, you’ll need to leverage Spectrum.
Spectrum serves as a global TCP and UDP proxy, operating on every Cloudflare’s PoP. Unlike HTTP/S traffic, Spectrum doesn’t terminate the connection by default; instead, it provides robust L3/L4 DDoS protection while efficiently passing packets through to the origin server. This enables secure and optimized handling of a diverse range of network protocols beyond traditional web traffic.
IP Access Rules & Network-layer DDoS Protection
As TCP/UDP operates at Layer 4, it’s important to note that the WAF does not apply to this type of traffic. In such cases, the use of IP Access Rules is recommended. In addition, one can overwrite the Network-layer DDoS Attack Protection managed ruleset. It’s worth mentioning that future plans might include extending support for Spectrum to incorporate the capabilities of Magic Firewall, a global network firewall.
Note: if a Spectrum application type TCP/UDP employs a proxied hostname as its origin, the traffic will eventually still traverse through the WAF. Furthermore, when configuring Spectrum with an application type of HTTP/S, it’s possible to define granular WAF Custom Rules with specific HTTP ports.
Use Case: SSL VPN#
To seamlessly set up most SSL VPNs, such as OpenVPN or Cisco AnyConnect, follow a straightforward setup by configuring two Spectrum applications:
- one TCP application
- one UDP application
Choose a preferred hostname, like openvpn.example.com. Set both Edge and Origin Port to 443 (default port for SSL VPNs). Specify the Origin Server IP where the VPN gateway resides.
Note: for dual-protocol VPNs involving both TCP and UDP, it’s crucial to acknowledge that, for a single VPN session, the egress IPs for TCP and UDP connections (source IP of connection from Cloudflare to origin) may differ. This occurs because these connections are likely served by different metals. Adjust VPN origin server policies to accommodate this variation, either by relaxing policies to accept different source IPs (typically within the same /24 IP prefix), or by configuring and leveraging the Proxy Protocol to match up connections. Additionally, be mindful of potential MTU adjustments, which may need to be set to MTU 1420 or lower in certain cases.
Here are some general advantages of utilizing VPN over Spectrum:
- Conceal internal VPN endpoints behind Anycast for added security through obscurity.
- Cloudflare Spectrum might offer improved speed, due to global network interconnects, and especially when paired with Argo Smart Routing.
- Benefit from Edge-based filtering, enabling configuration and tuning options such as IP Access Rules for TCP apps and Network Analytics for comprehensive logging.
This approach not only streamlines the integration of SSL VPNs but also presents additional advantages in terms of security, speed, and configuration flexibility.
L3 Network#
Magic Transit – IP network security and performance
When organizations seek to fortify their entire networks or entire IP prefixes, IT departments often resort to conventional hardware solutions or cloud scrubbing providers. Magic Transit emerges as a comprehensive network security solution, delivering DDoS protection, traffic acceleration, and more, accessible from every Cloudflare PoP. This applies seamlessly to on-premise, cloud-hosted, and hybrid network environments.
Note: certain prerequisites are essential for utilizing Magic Transit, typically involving an IPv4 IP prefix length requirement of a minimum
/24, due to how Border Gateway Protocol (BGP) works. However, those unable to meet this requirement can explore the option of Cloudflare IPs, or even Spectrum to protect only single IP addresses. In certain cases one can also directly connect their network infrastructure with Cloudflare with Network Interconnect for a more reliable and secure experience.
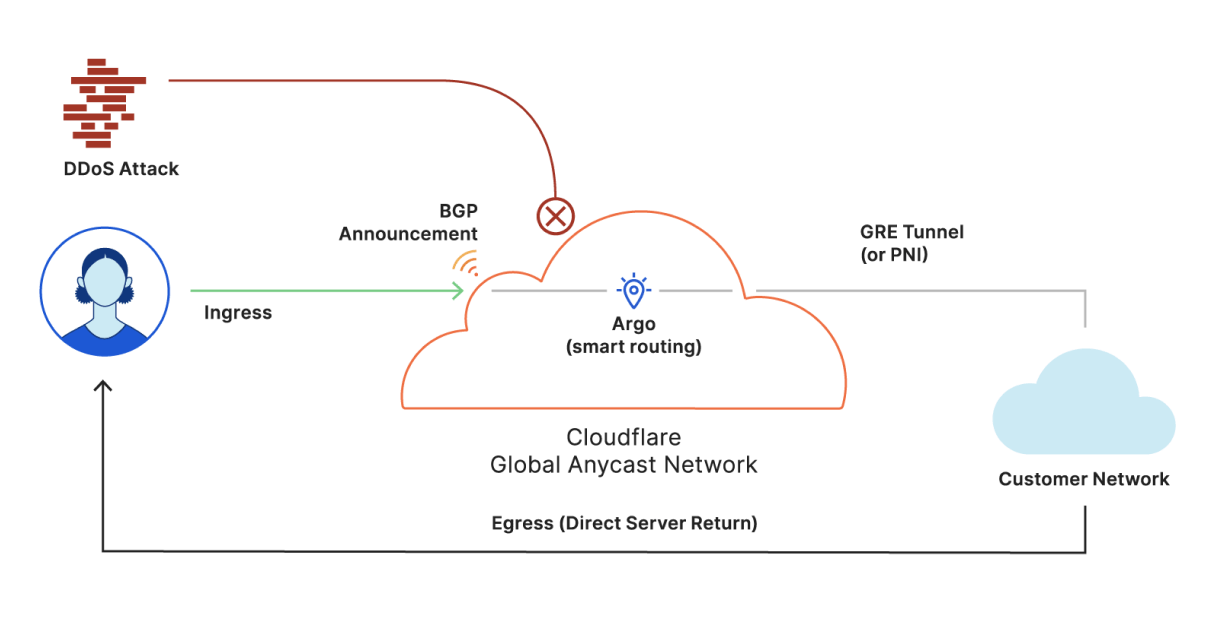
Image Source: Magic Transit Reference Architecture
For nearly real-time insights into network and transport-layer traffic patterns, as well as DDoS attacks, explore Network Analytics. Moreover, you can enhance your visibility into network traffic by configuring Magic Network Monitoring to analyze the network flow data transmitted from a your routers.
Magic Firewall – Firewall-as-a-Service (FWaaS)
Beyond DDoS protection, Magic Transit incorporates a version of Magic Firewall – a Firewall-as-a-Service (FWaaS) solution. This network firewall allows you to apply filter rules based on various criteria, including protocol and packet length. By filtering undesirable traffic before it reaches your network, Magic Firewall acts as an additional global proactive defense mechanism, stopping attacks before they reach your network.
Use Case: CIDR /24#
TBD
Monitoring & Troubleshooting#
- Periodically monitor and review your general setup with the Security Center, the Zone Security Analytics, and set up Notifications for important updates or incidents.
Note: Obviously also secure your Cloudflare account with 2FA, considering the Principle of Least Privilege, and periodically reviewing your account Audit Logs.
Push all raw logs to a storage service, SIEMs, or log managemenet service with Logpush. Review my Cloudflare Logpush article for more details and setup examples.
Set up standalone Health Checks to monitor whether an IP address or hostname is online. Additionally, the analytics show average latency – measured in round-trip time (RTT) — for individual origins over time.
For a broader overview of security and attacks specific to countries, routing, or outages, explore Cloudflare Radar. Check out the Year in Review 2023 report.
For anything troubleshooting-related, explore the Troubleshooting section, Cloudflare Trace, or contact Cloudflare Support.
Compliance#
Note: each legal entity bears the responsibility for ensuring its own compliance and adherence to legal practices within its respective jurisdictions.
Cloudflare can provide necesssary compliance documentation for audits or due diligence. Most documentation can also be found online, such as Privacy Policy, Data Processing Addendum (DPA), Self-Serve Subscription Agreement, Enterprise Subscription Terms of Service, and the Data Privacy Framework (DPF), according to European Commission adopting new adequacy decision for safe and trusted EU-US data flows.
Additionally, the Data Localization Suite (DLS) provides three features designed to address data residency requirements, if necessary:
- Geo Key Manager: control where the TLS keys are stored.
- Regional Services: control where the TLS termination / processing occurs.
- Customer Metadata Boundary: control where Customer Logs (metadata) are stored.
Review the Cloudflare Trust Hub for more detailed information.
Learn more about Cloudflare’s Impact, Commitments, Privacy-preserving Products, Research, and more.
Final Remarks#
Security is not a simple flip of a switch; it’s built through processes and layers. The more layers you incorporate, the stronger your security posture becomes.
Embark on securing your web applications (Layer 7), API endpoints (Layer 7), TCP/UDP services (Layer 4), and IP prefixes (Layer 3) today with the deployment of a comprehensive layered security solution.
Get started with the Cloudflare Learning Paths!
Alternatively, if you’re looking to extend security to your employees, devices, internal networks, and enterprise applications, delve into the comprehensive offerings of Cloudflare’s SSE & SASE Platform, also known as Cloudflare One.
Cloudflare One is built on Cloudflare’s connectivity cloud, a unified, intelligent platform of programmable cloud-native services that enable any-to-any connectivity between all networks (enterprise and Internet), cloud environments, applications, and users.
Explore building and developing Full-Stack applications with Pages for deploying static front-end websites, Workers for implementing serverless code and dynamic computing, and a range of innovative storage solutions.
Though Cloudflare Workers behave similarly to JavaScript in the browser or in Node.js, there are a few differences in how you have to think about your code. Under the hood, the Workers runtime uses the V8 engine — the same engine used by Chromium and Node.js. The Workers runtime also implements many of the standard APIs available in most modern browsers.
For those intrigued by Artificial Intelligence (AI), delve into the intersection of cybersecurity and AI in the insightful Cybersecurity and Artificial Intelligence (AI) article.
Disclaimer#
Educational purposes only. Several parts are over-simplified, for showcasing purposes.
This blog post is independent and not affiliated with, endorsed by, or necessarily reflective of the opinions of Cloudflare or any other entities mentioned.
Certain content, images, and screenshots are sourced from publicly available resources.
