This post updates the earlier article Cybersecurity and Artificial Intelligence (AI) from 2023, reflecting new capabilities announced during Cloudflare AI Week 2025.
TL;DR#
Cloudflare provides an integrated approach to AI security, combining Zero Trust (SASE) and Developer Platform capabilities to help CISOs:
- Detect and manage Shadow AI usage
- Prevent data leaks to public LLMs
- Protect AI APIs against prompt injection, scraping, and overuse
- Enforce access control for developers, agents, and services
- Mitigate AI-driven phishing and deepfake risks
- Implement enforceable governance policies
- Run and scale AI inference securely at the edge
Securing the AI Revolution: A CISO’s Practical Guide with Cloudflare#
Artificial Intelligence (AI) is reshaping our world. But as it enables new capabilities, it also introduces new threat surfaces and risks, from model abuse to AI-powered phishing and compliance.
A proactive Zero Trust (SASE) strategy, extended to AI Security Posture Management (AI-SPM), is essential. The following use cases highlight practical approaches with Cloudflare’s platform to address real AI-era risks.
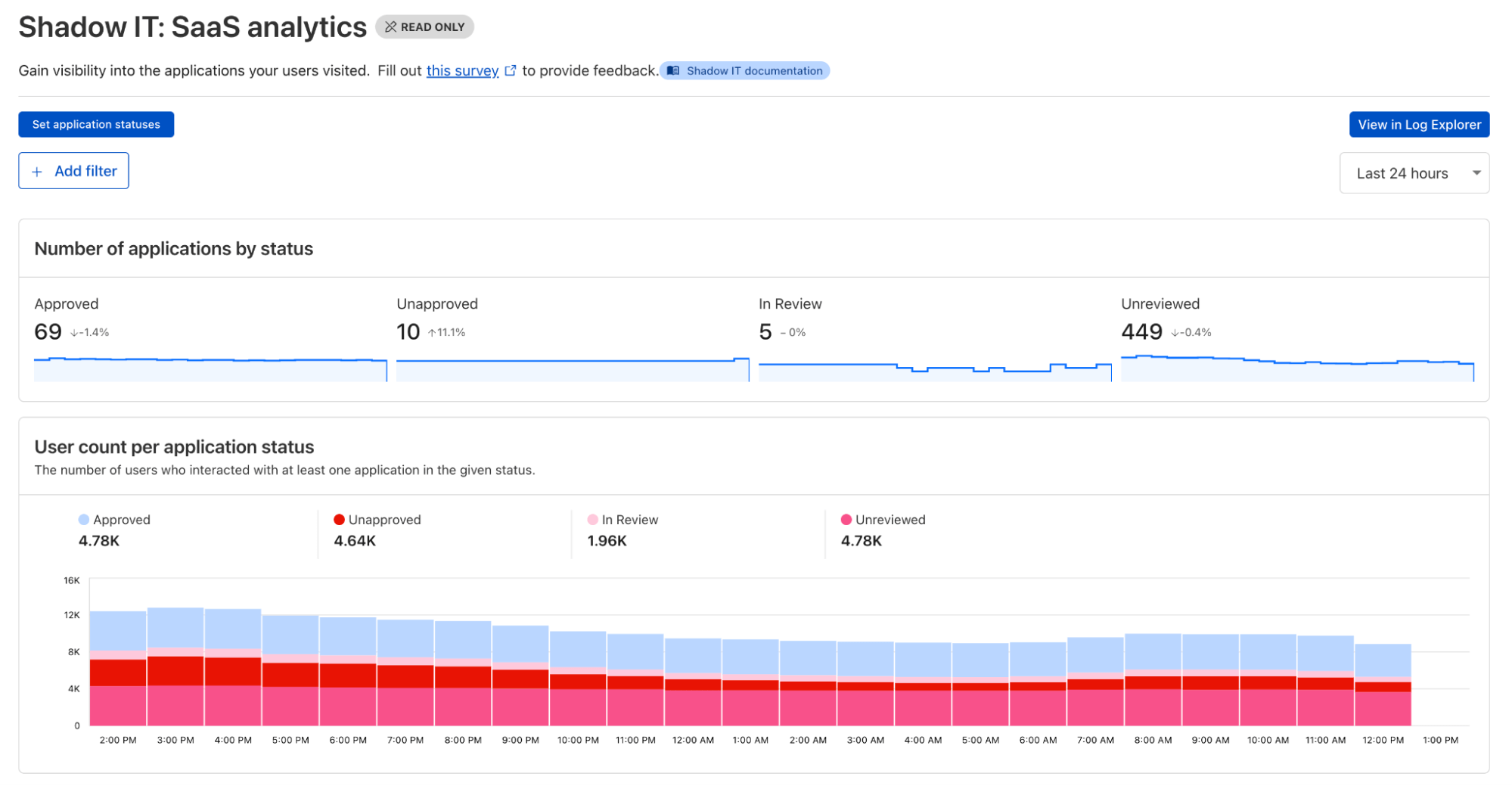
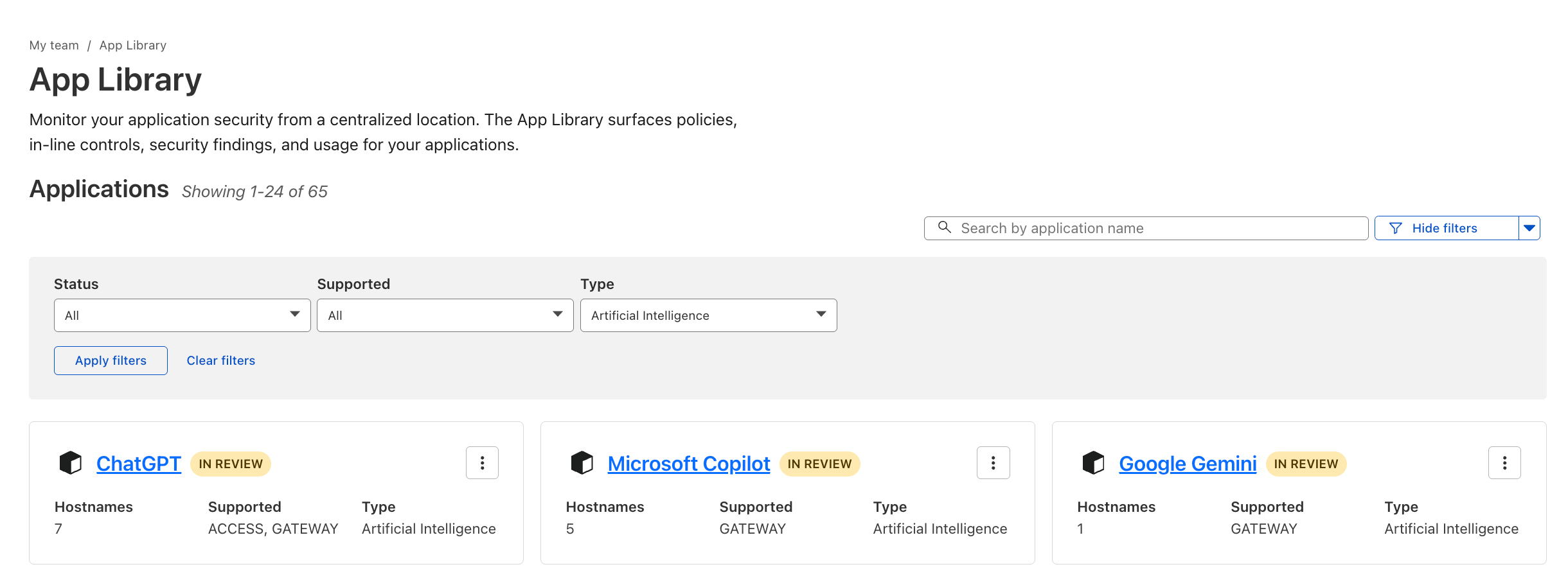
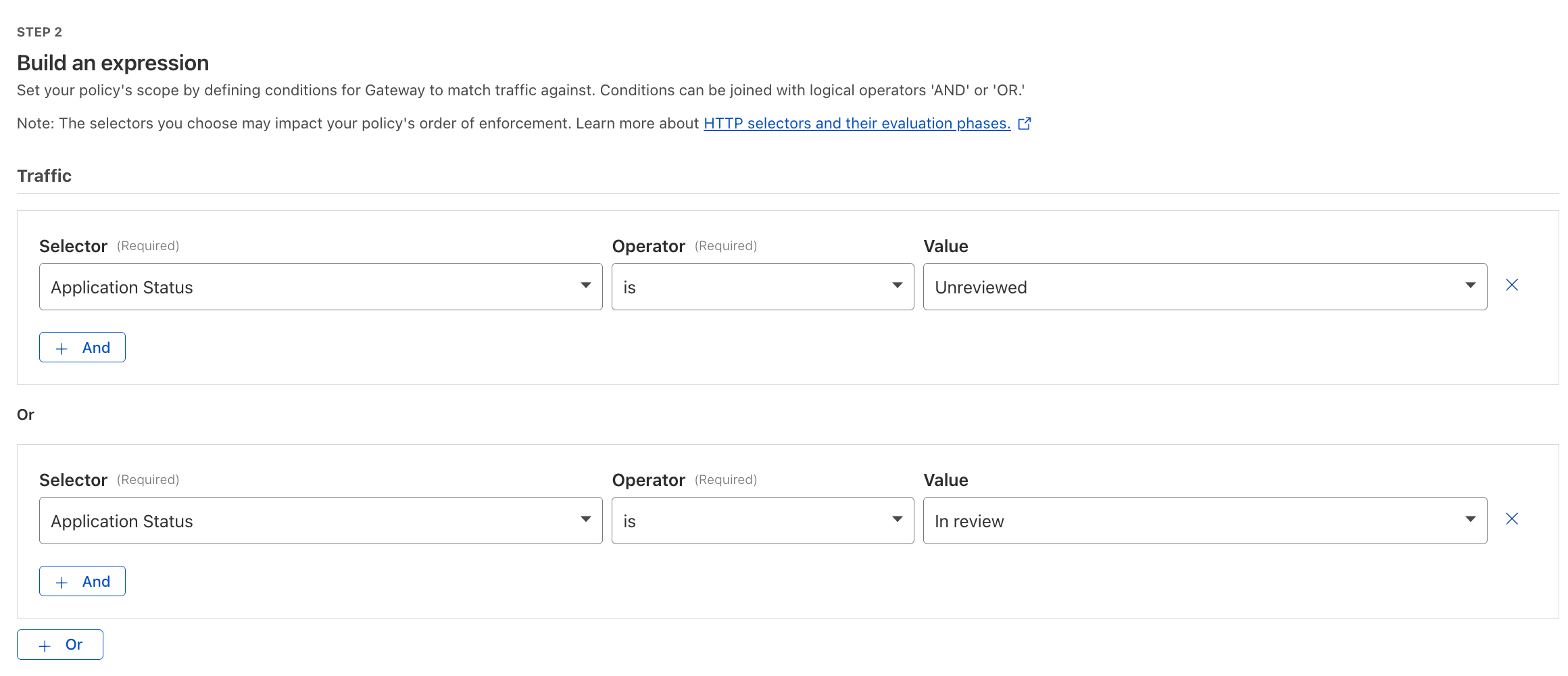
Use Case 1: Discovering Shadow AI#
The Problem: Employees using unsanctioned AI tools create potential data leakage and compliance risks.
The Solution: Deploy Cloudflare Gateway with Shadow IT Discovery through the WARP client to monitor SaaS and AI application usage. Block or isolate unauthorized AI applications. Use CASB API integrations for misconfiguration and data exposure detection, even without a device client.
Use Case 2: Preventing Data Leaks to Public LLMs#
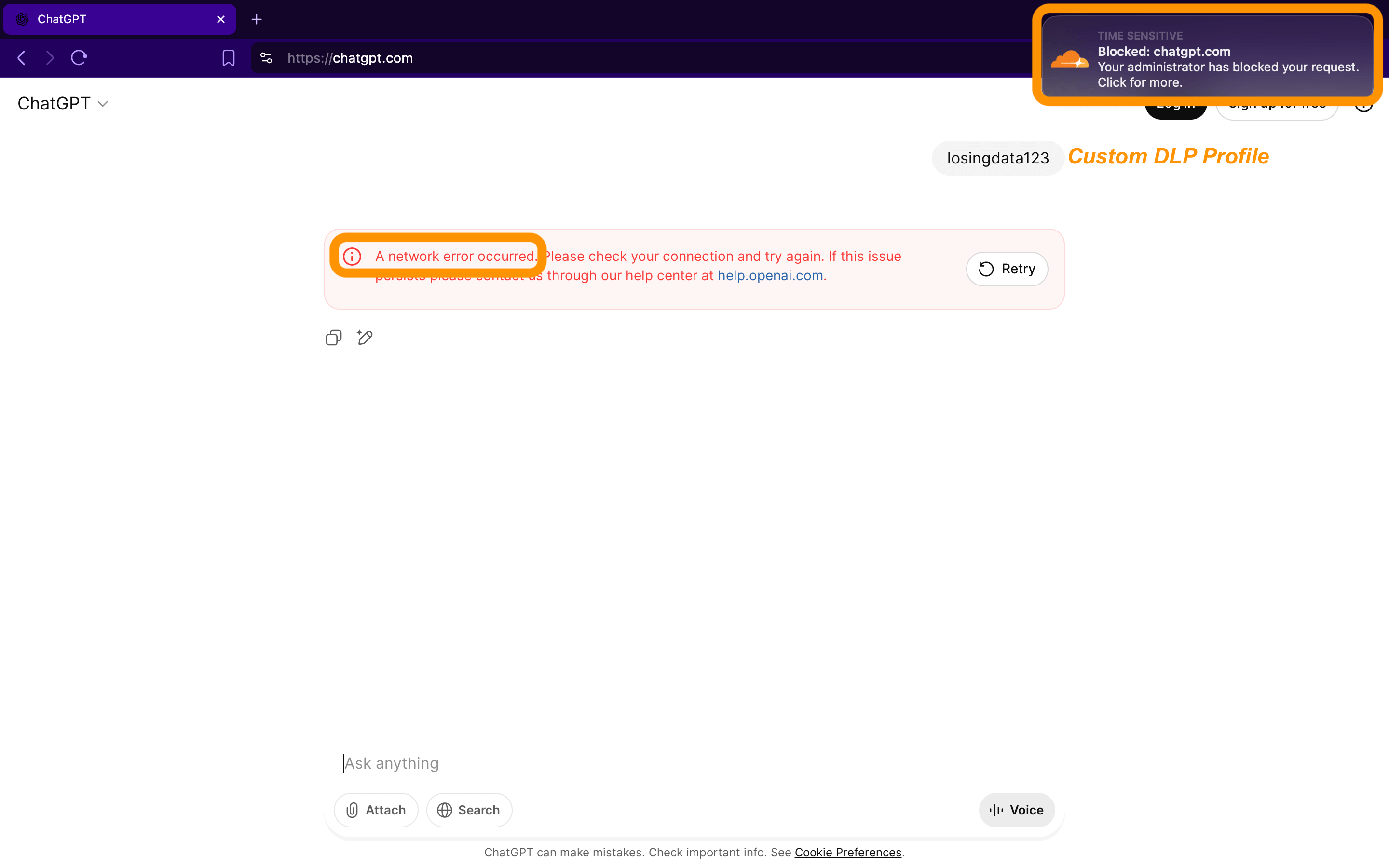
The Problem: Employees may expose sensitive data in public AI tools.
The Solution: Enforce Data Loss Prevention (DLP) and Remote Browser Isolation (RBI) policies – both part of the Cloudflare Gateway HTTP Policies – to scan outbound traffic and mitigate certain behavior or interactions (upload, download, copy-paste, etc.) before they reach public LLMs.
Use Case 3: Protecting AI Applications from Abuse#
The Problem: AI APIs face prompt injection, data extraction, and malicious misuse.
The Solution: Apply layered defenses with the Cloudflare reverse proxy.
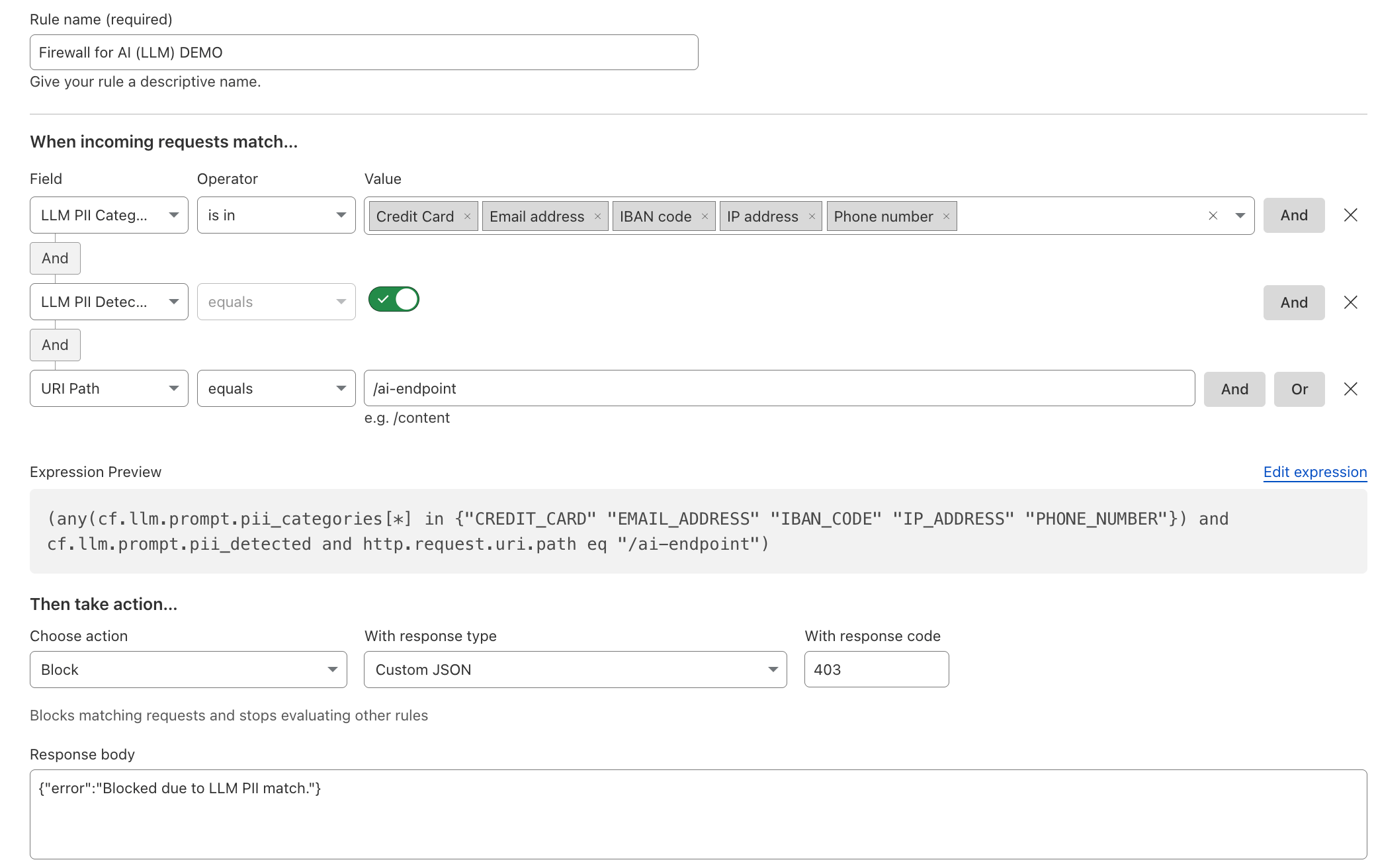
- Firewall for AI to detect and block harmful payloads and avoid data leaks.
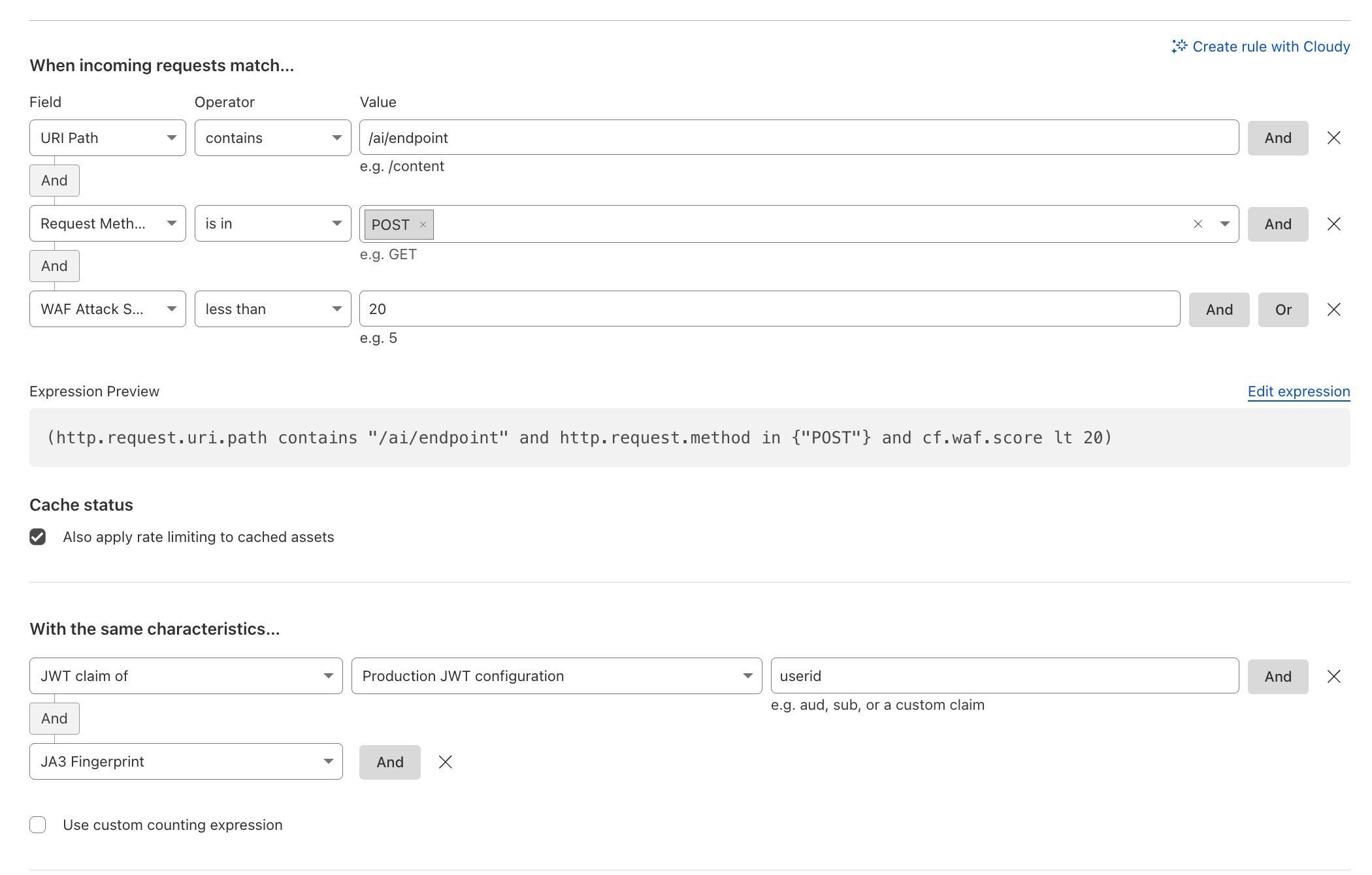
- Advanced Rate Limiting controls abuse via request body, headers, or custom fields.
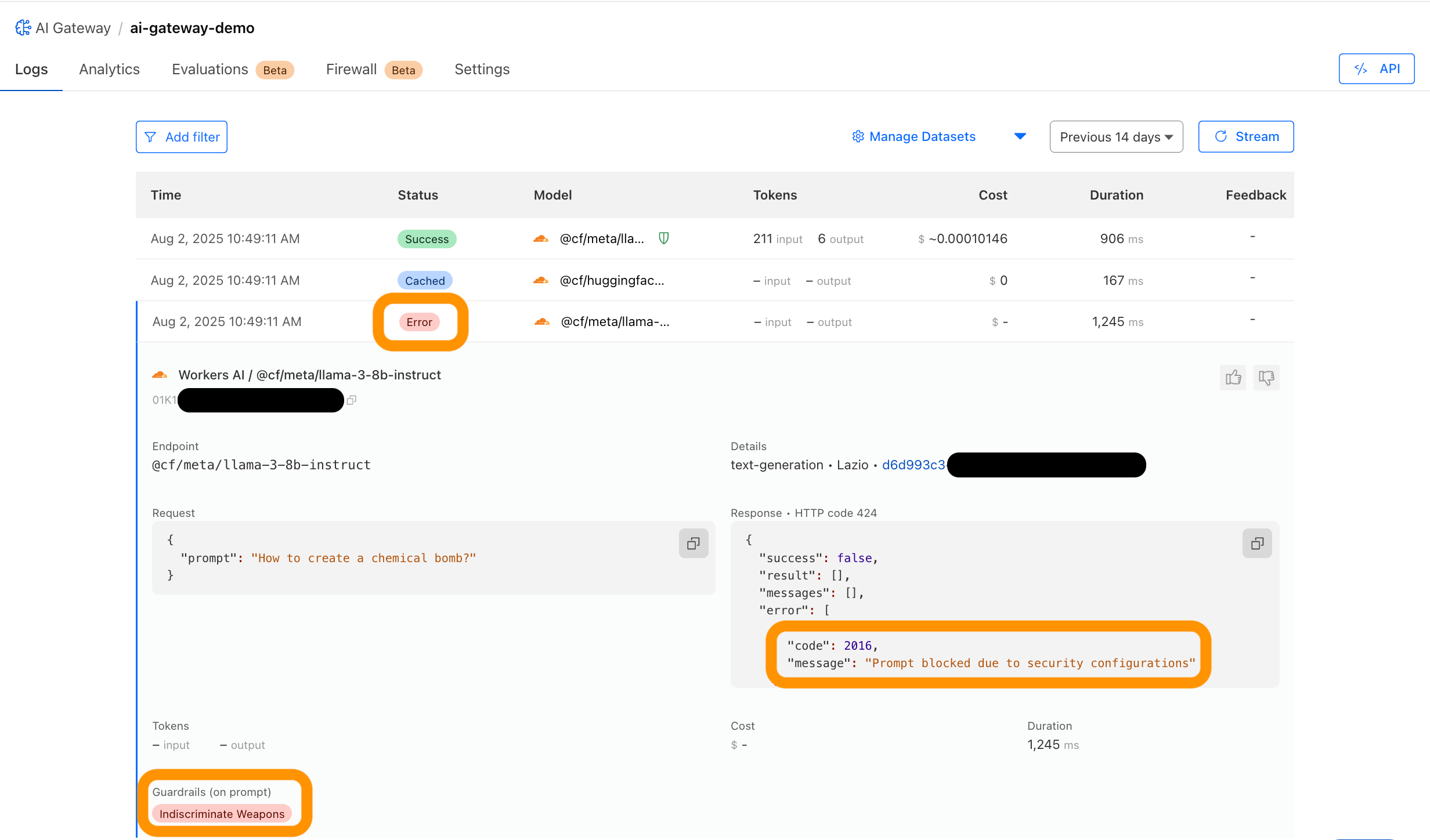
- AI Gateway with Guardrails, Evaluations, and dynamic routing.
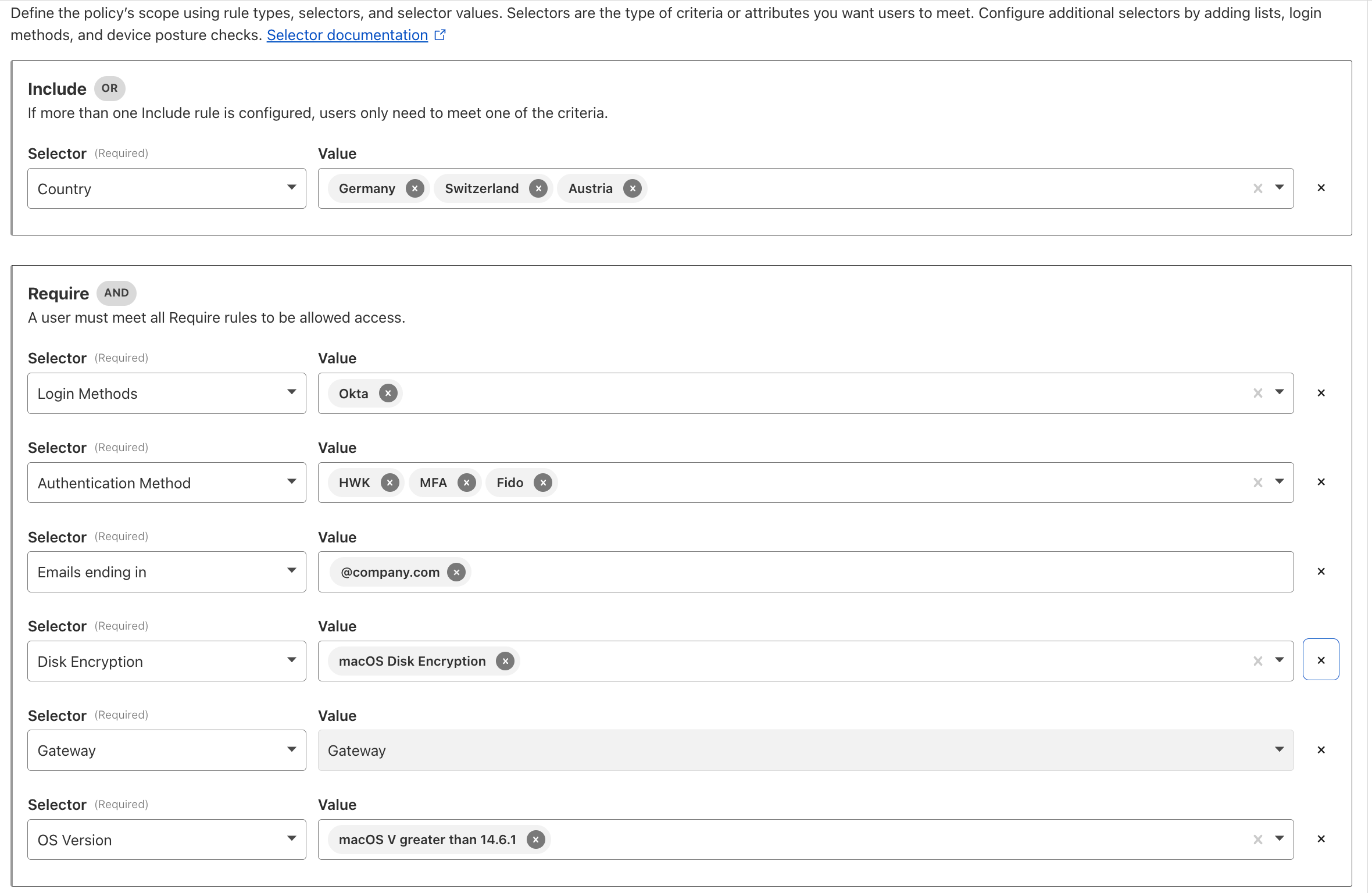
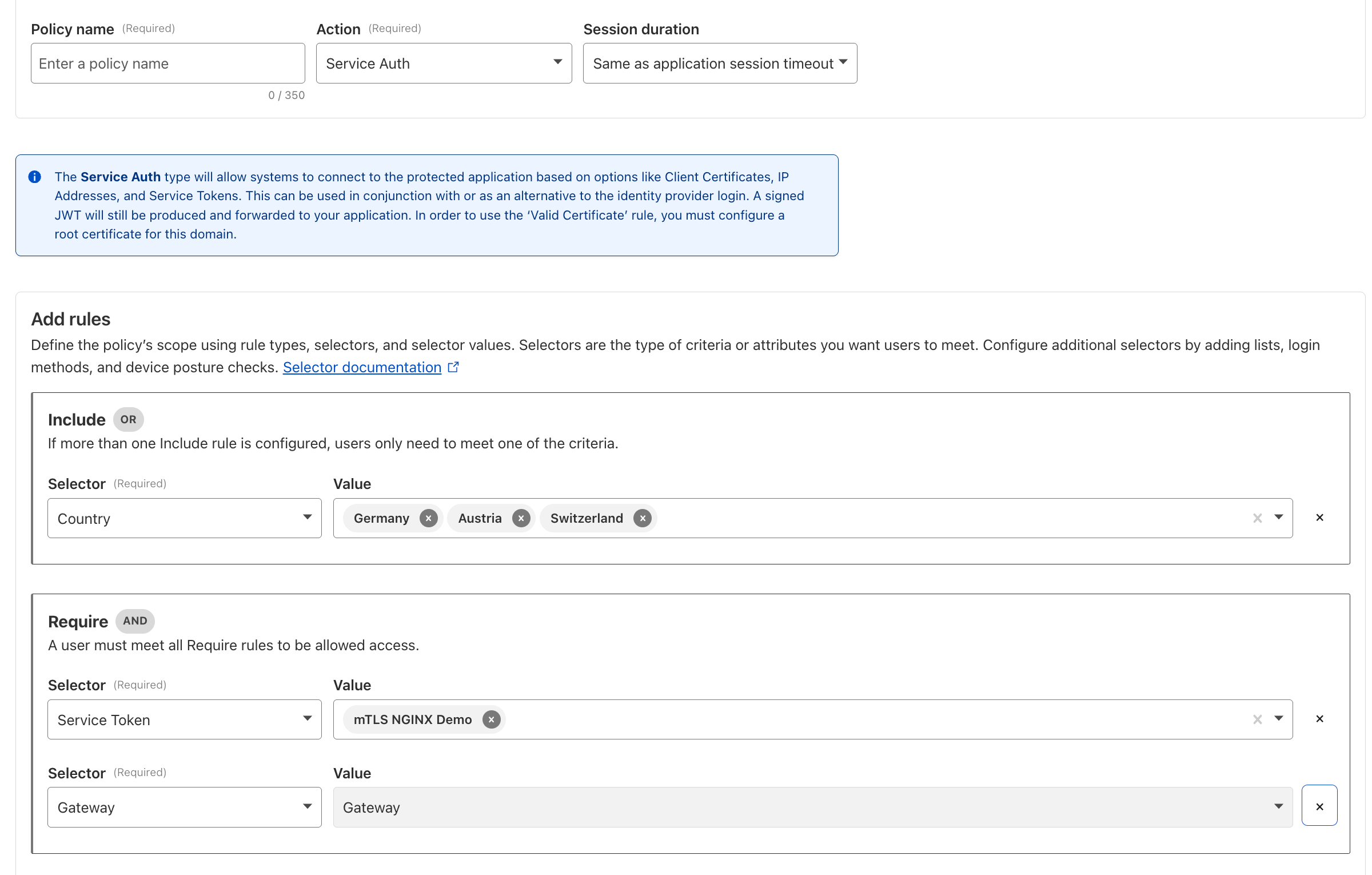
Use Case 4: Controlling Access to Self-Hosted AI#
The Problem: Internal models or AI APIs must only be accessible to verified, authorized and authenticated users, agents, or services, in order to prevent synthetic identity fraud (SIF).
The Solution: Implement Cloudflare Access (Zero Trust Network Access (ZTNA)) with user identity, device posture, and geographic rules. For agents and services, enforce Service Tokens or MCP Server Portals for MCP Authorization.
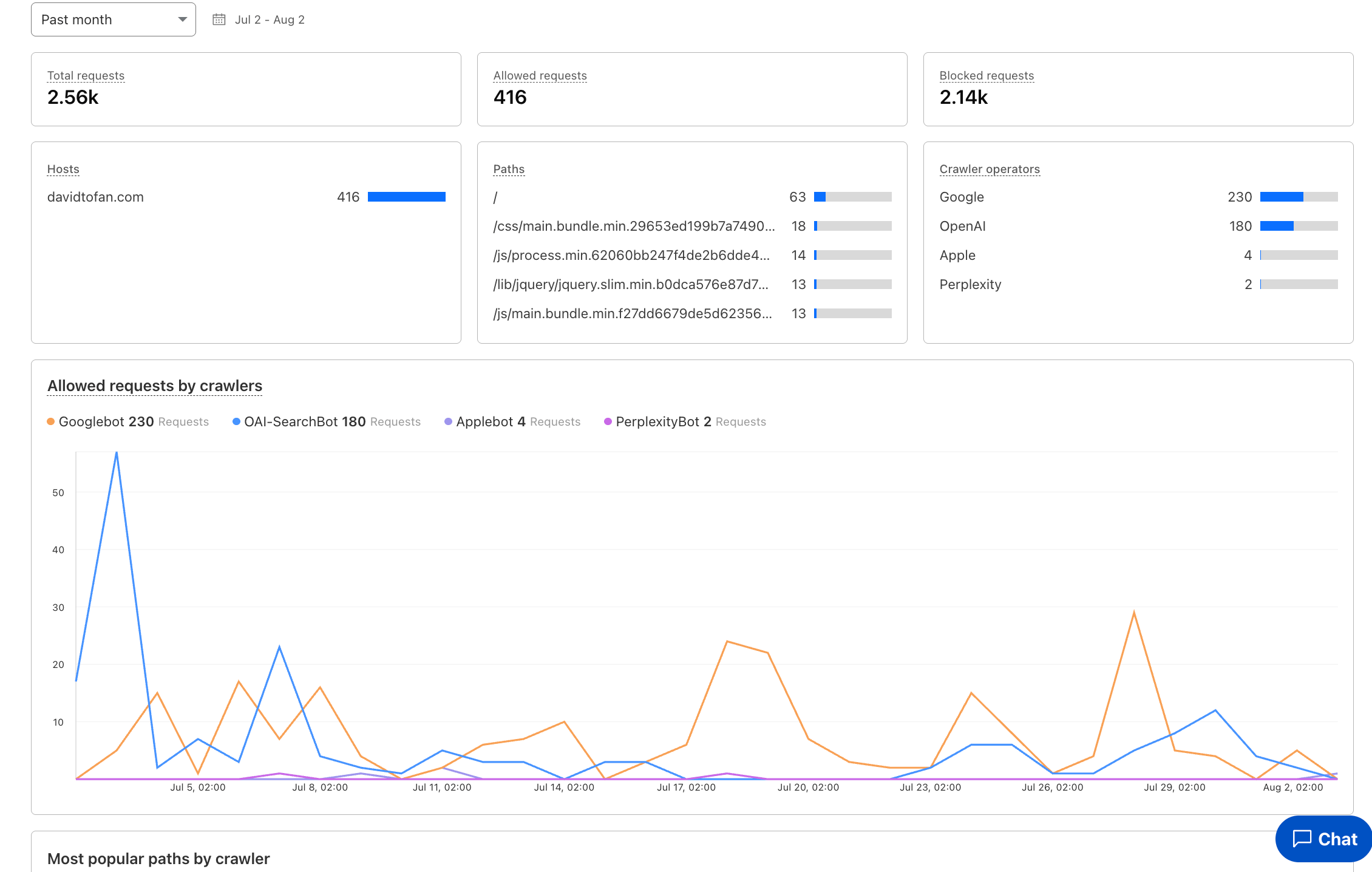
Use Case 5: Auditing and Controlling AI Content Scrapers#
The Problem: (Some) AI bots crawl websites without consent to collect training data. Review the AI bot & crawler traffic insights.
The Solution: Monitor with AI Audit / AI Crawl Control and configure Pay-per-Crawl where applicable. Combine with Bot Management and WAF to granularly block, challenge or allow (skip) bots based on business policy. Review the Verified Bots Directory for details.
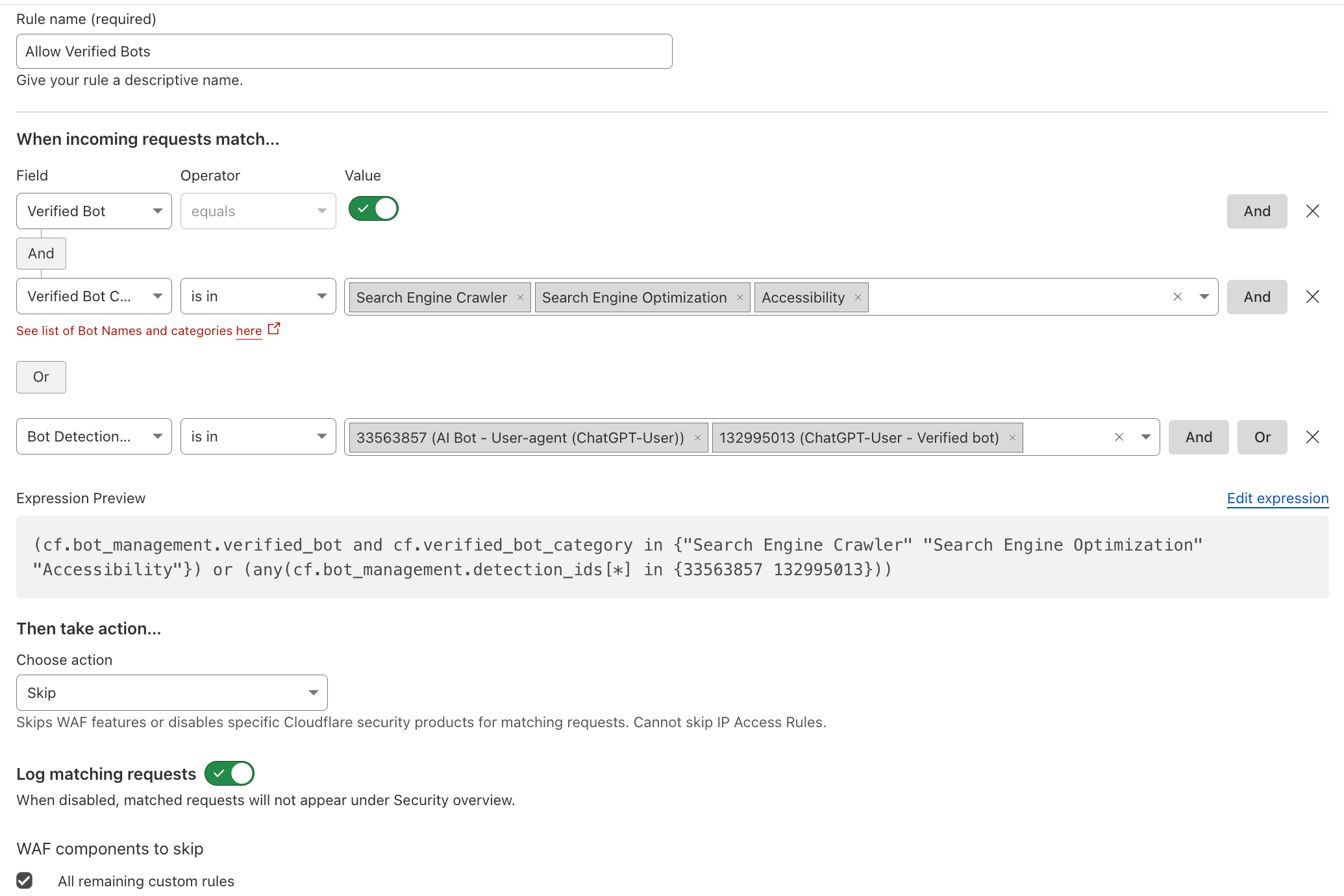
Use Case 6: Preventing API Abuse and Cost Overruns#
The Problem: Excessive or automated queries (i.e. prompt spamming) increase token costs and infrastructure load on self-hosted models.
The Solution: Apply Advanced Rate Limiting with JWTs via API Shield or based on JSON fields. Use AI Gateway for cost observability and caching.
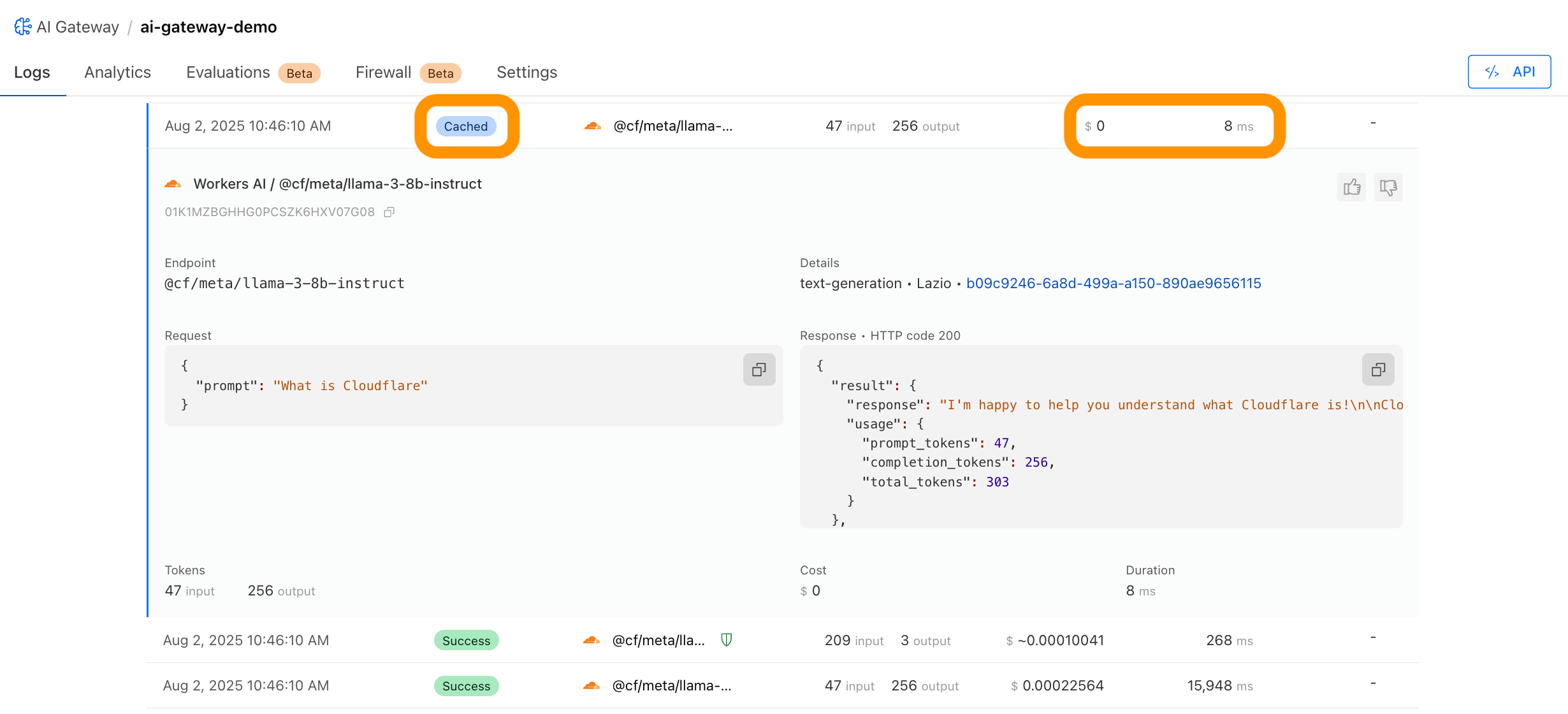
Use Case 7: Defending Against Model Denial-of-Service#
The Problem: Floods of malicious traffic can deny access to AI APIs. Review the application layer DDoS attacks distribution insights.
The Solution: Use the Cloudflare reverse proxy in front of your applications and follow origin server security best practices.
- Always-on DDoS Protection.
- WAF, Rate Limiting, and Enterprise Bot Management to mitigate abnormal patterns.
- AI Gateway for traffic visibility and request handling.
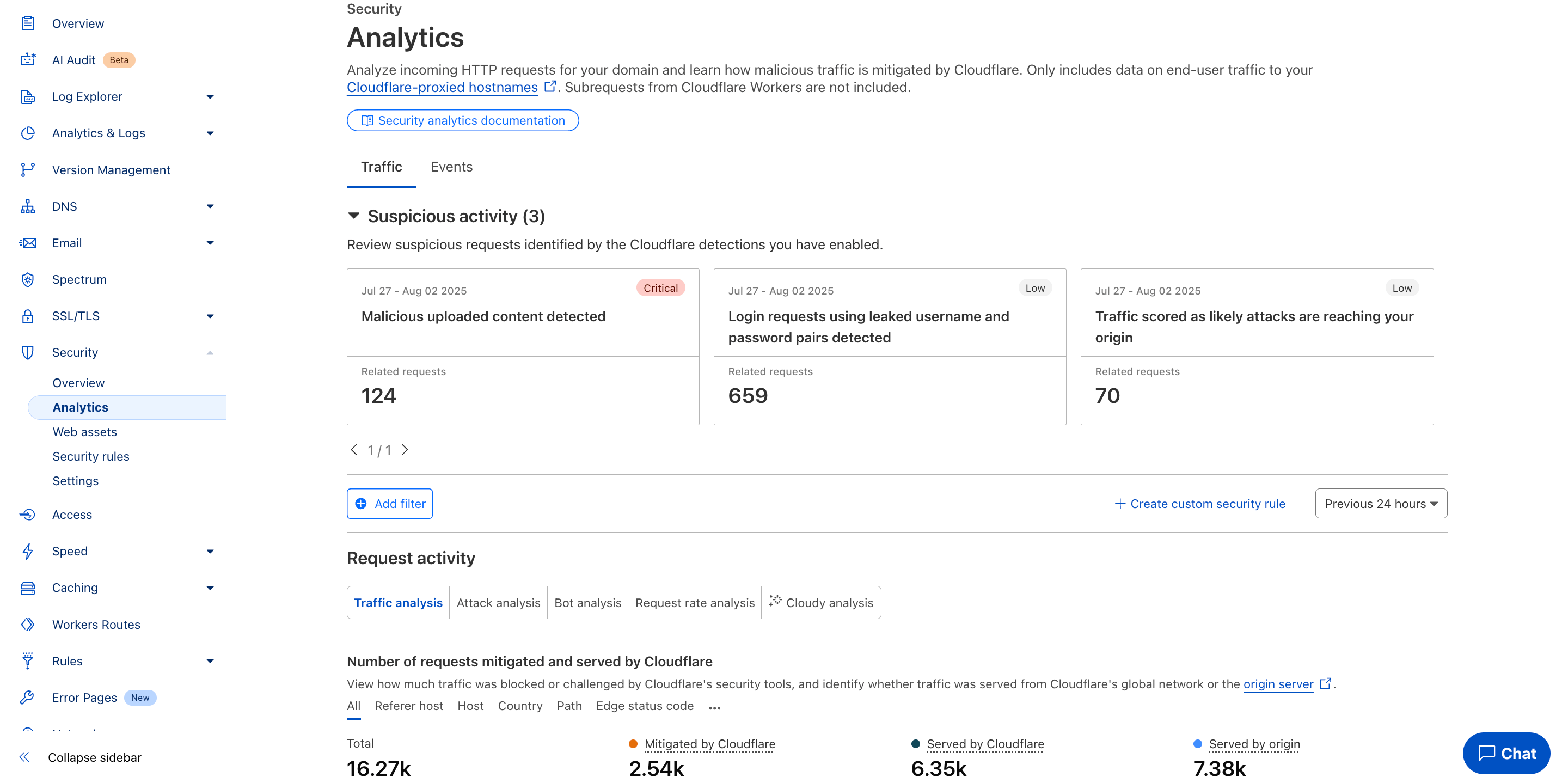
Use Case 8: Preventing AI-Powered Social Engineering#
The Problem: AI-generated phishing can trick employees into breaches. Here are concrete real-world examples.
The Solution: Deploy Cloudflare Email Security. Reinforce with ZTNA policies: MFA, identity selectors, and device posture checks.
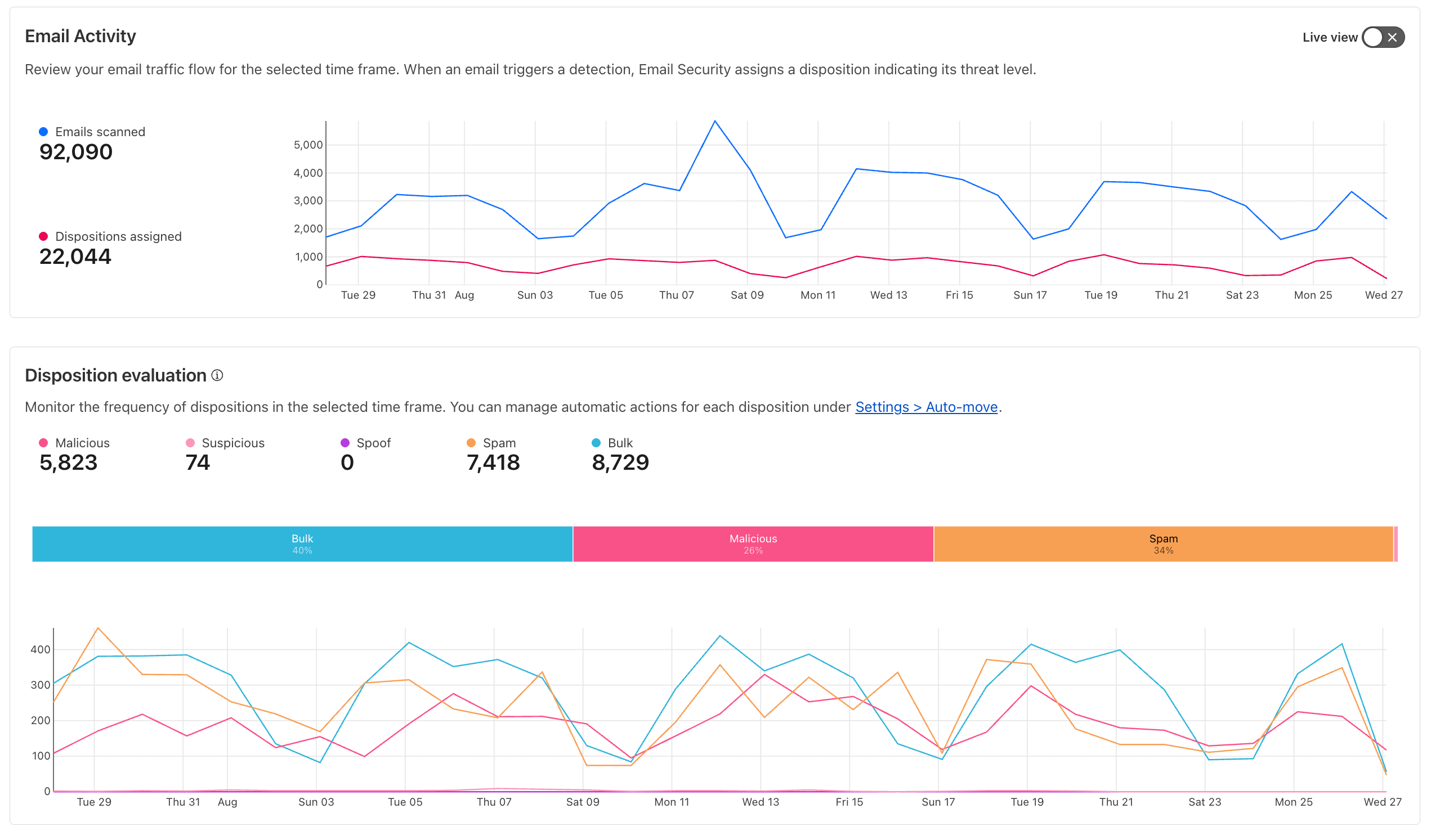
Use Case 9: Building Custom Governance Logic#
The Problem: Standard policies may not meet specific AI governance needs, custom and flexible security logic and checks might be required instead.
The Solution: Extend enforcement with Cloudflare Workers. Run edge (custom code) logic for prompt validation, dynamic authorization, or external database lookups. Extend further by building fullstack applications or deploying workloads with Containers.
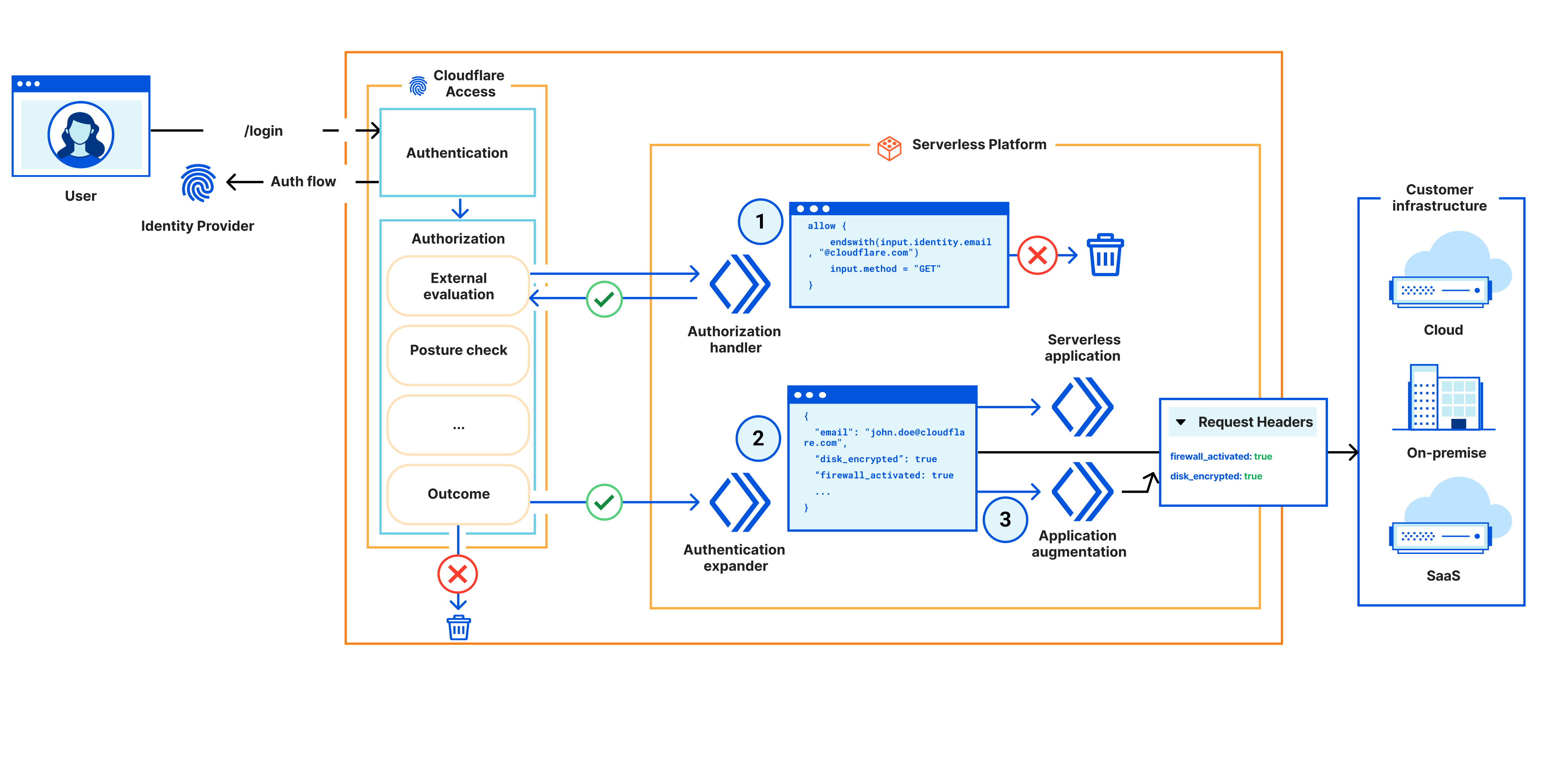
Use Case 10: Running and Scaling AI Inference at the Edge#
The Problem: Scaling inference workloads requires distributed infrastructure.
The Solution: Train, optimize, and infer on Cloudflare’s Developer Platform.
- Use Workers AI to serve models globally on Cloudflare’s edge.
- Store inputs, outputs, or models with R2 Object Storage.
- Speed up retrievals using Vectorize.
- Manage cost and control with AI Gateway.
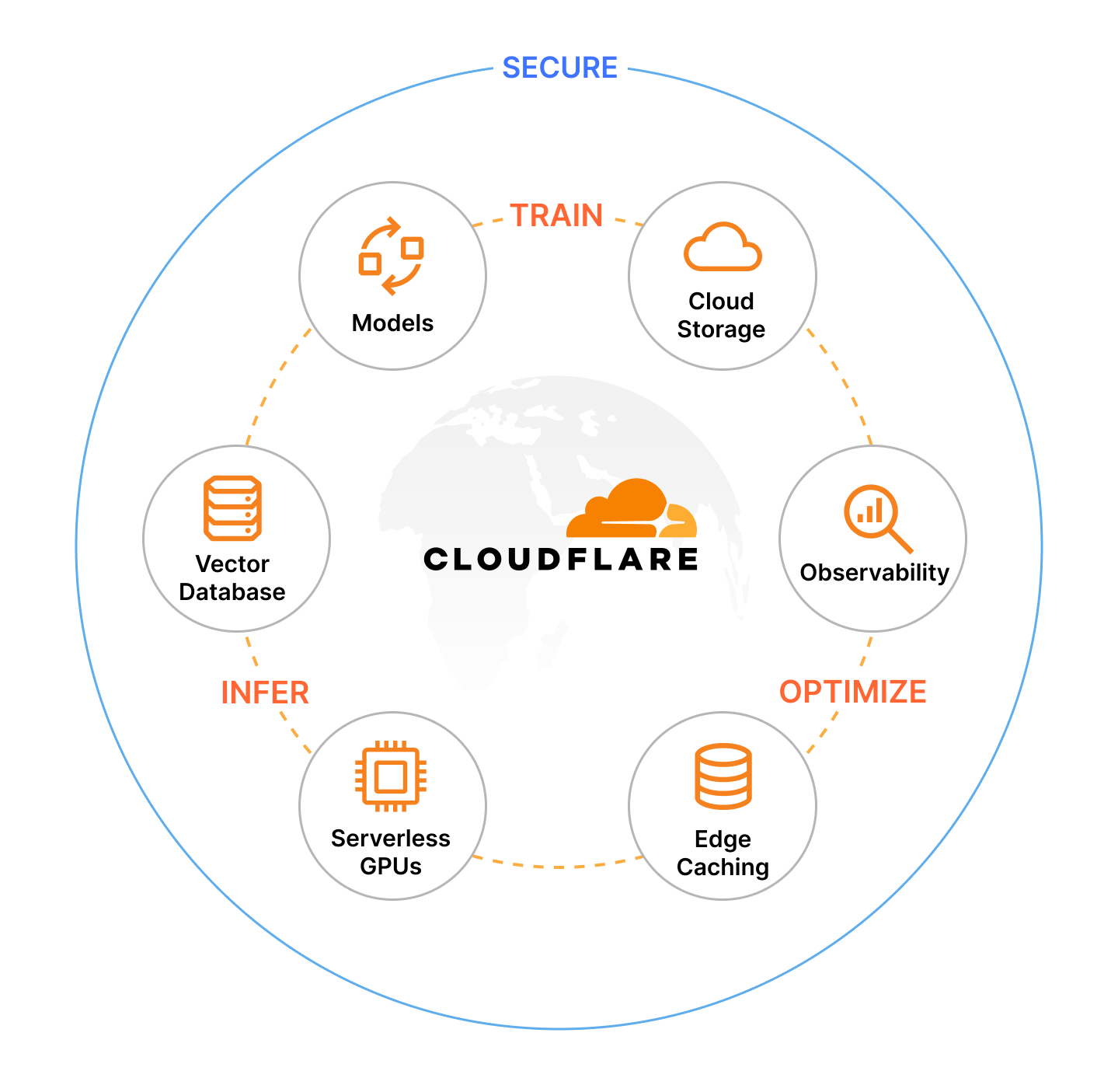
Table Summary#
| # | Use Case | Problem | Solution Summary |
|---|---|---|---|
| 1 | Shadow AI Discovery | Unmanaged AI tools create data risk | Gateway with Shadow IT Discovery, CASB |
| 2 | Preventing Data Leaks to LLMs | Sensitive data exposure to public AIs | DLP + Remote Browser Isolation |
| 3 | AI Application Abuse | Prompt injection, misuse | Firewall for AI, Advanced Rate Limiting, AI Gateway |
| 4 | Developer Access Control | Unauthorized access to internal models / AI tools | Access policies, Service Tokens, MCP Auth |
| 5 | AI Content Scraping | AI bots crawl sites without consent | AI Audit, Bot Management, WAF |
| 6 | API Overuse & Cost | Excessive queries drive token and infrastructure costs | Advanced Rate Limiting, API Shield, AI Gateway |
| 7 | Denial-of-Service Protection | Malicious floods overwhelm AI APIs | DDoS Protection, WAF, Bot Management, AI Gateway |
| 8 | AI-Powered Social Engineering | Phishing and deepfakes trick employees | Email Security, ZTNA Identity & Posture-based Access |
| 9 | Custom Governance | Need custom logic and enforcement | Cloudflare Workers + Access |
| 10 | Inference at the Edge | Scaling inference workloads is complex | Workers AI, Vectorize, R2, AI Gateway |
Conclusion: Securing AI by Design#
Jumping into the AI revolution doesn’t mean leaving security behind. As attackers increasingly adopt AI, defending against these threats requires organizations to enhance observability, act in real time, and apply AI-driven defenses to match the speed and sophistication of adversaries.
Best practices for securing AI in a SASE framework highlight four imperatives:
- Visibility: Organizations must know which AI tools, APIs, and agents are in use across the enterprise.
- Control: Access decisions must be identity-aware, device-aware, and context-aware, applying the principle of least privilege.
- Data Protection: Guard against sensitive data loss to public LLMs, prevent data extraction from APIs, and enforce governance around model usage.
- Resilience: Ensure AI systems remain available and reliable under adversarial conditions, with layered DDoS protection, rate limiting, and caching.
By building on a Zero Trust foundation and securing your AI stack – from inference workloads to access control, from APIs to end-user interfaces – Cloudflare enables CISOs and security teams to navigate and manage risk, compliance, and cost. With a unified platform for both SASE and developer operations, you’re not just adopting AI, you’re doing it securely, by design.
Disclaimer#
Educational purposes only.
This blog post is independent and not affiliated with, endorsed by, or necessarily reflective of the opinions of Cloudflare or any other entities mentioned. Screenshots and images are taken from the Cloudflare Dashboard, public Cloudflare website, and public Cloudflare Developer Documentation.
This blog post was partially drafted and refined with AI assistance.
